Investigating Android TeleGuard
18/04/2025 Friday
Android TeleGuard is a messaging app developed by Swisscows with a
strong focus on user privacy. According to its developers, the app
stores chats on the server only until they are delivered and does not
share data with third parties. All communications through the app are
end-to-end encrypted. TeleGuard is a cross-platform application
available for Android, iOS, and Windows operating systems.
Digital Forensics Values of Android TeleGuard
Since the app deletes all chats after they are delivered, the only way
to retrieve the data is by extracting it from the device where the
communication took place. This significantly raises the forensic value
of the artifacts left behind by Android TeleGuard. As shown below, the
extracted data may contain important information that can help
investigators gather details about the communications of suspicious
individuals.
Location of Android TeleGuard
Android TeleGuard artifact can be found at the following locations:
*/data/ch.swisscows.messenger.teleguardapp/app_flutter/teleguard_database.db
*/data/ch.swisscows.messenger.teleguardapp/app_flutter/teleguard_temp.db
*/data/ch.swisscows.messenger.teleguardapp/databases/download_tasks.db
Analyzing Android TeleGuard Artifacts with ArtiFast
This section will discuss how to use ArtiFast to extract Android
TeleGuard artifacts from Android machines’ files and what kind of
digital forensics insights we can gain from the artifact.
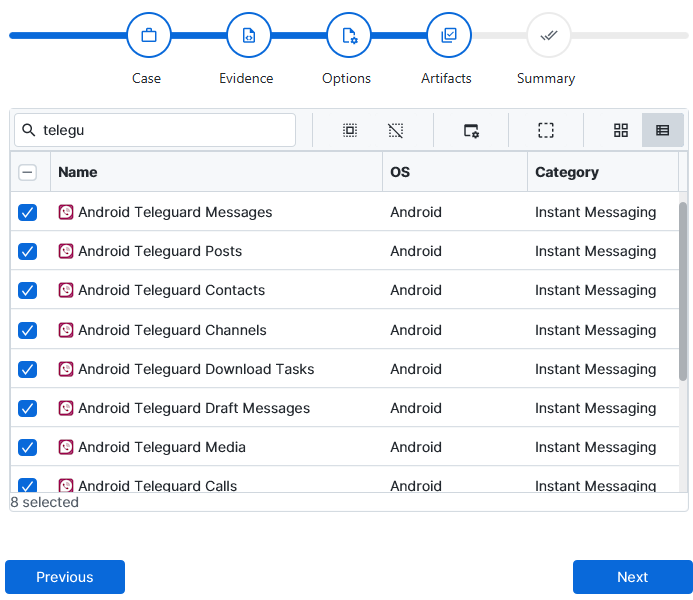
After you have created your case and added evidence for the
investigation, at the Artifact Selection phase, you can select Android
TeleGuard artifact parser:
×
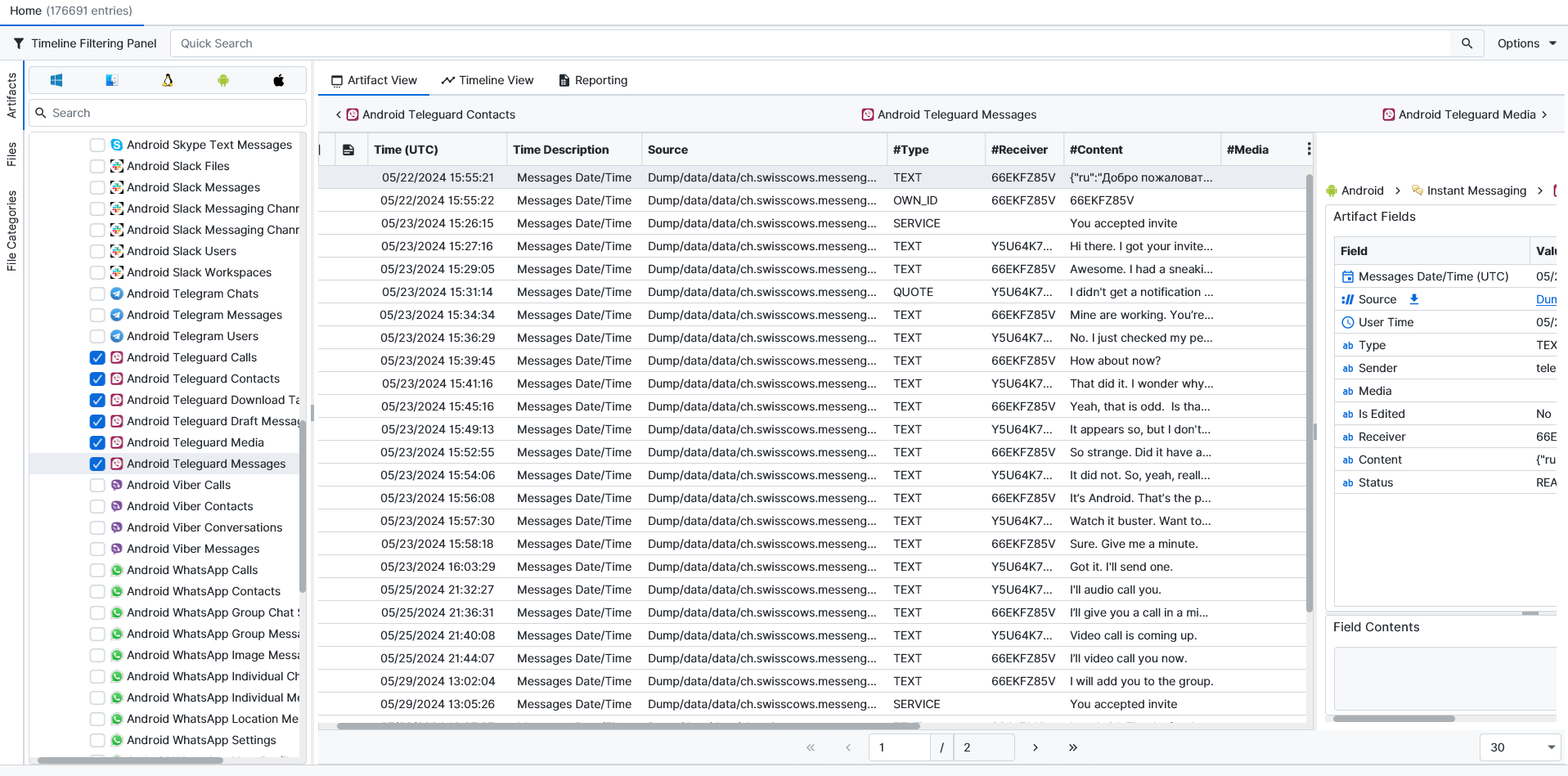
Once ArtiFast parsers plugins complete processing the artifact for analysis, it can be reviewed via “Artifact View” or “Timeline View,” with indexing, filtering, and searching capabilities. Below is a detailed description of Android TeleGuard artifacts in ArtiFast.
Android Teleguard Messages
- Message Date/Time: Messages Date/Time.
- User Time: User Time.
- Type: Type.
- Sender: Sender.
- Receiver: Receiver.
- Content: Content.
- Media: Media.
- Status: Status.
- Is Edited: Is Edited?
Android Teleguard Posts
- Posting Date/Time: Posting Date/Time.
- Channel ID: Channel ID.
- Header: Header.
- Content: Content.
- Type: Type.
- Local Status: Local Status.
- Views Count: Views Count.
- Likes Count: Likes Count.
- Dislikes Count: Dislikes Count.
- Metadata: Metadata.
- Media: Media.
Android Teleguard Contacts
- Last Activity Date/Time: Last Activity Date/Time.
- Server ID: Server ID.
- Alias: Alias.
- Type: Type.
- Color: Color.
- Avatar: Avatar.
- Options: Options.
- Info: Info.
- Last Visit Date/Time: Last Visit Time.
- Personal ID: Personal ID.
Android Teleguard Channels
- ID: ID.
- Alias: Alias.
- Description: Description.
- Category: Category.
- Color: Color.
- Avatar ID: Avatar ID.
- Subscribers Count: Subscribers Count.
- Admin: Admin.
- Posts Count: Posts Count.
- Is Deleted: Is Deleted.
- Language: Language.
- Type: Type.
Android Teleguard Download Tasks
- Task ID: Task ID.
- URL: URL.
- Status: Status.
- Progress: Progress.
- File Name: File Name.
- Saved Directory: Saved Directory.
- Headers: Headers.
- Mime Type: Mime Type.
- Resumable: Resumable.
- Show Notification: Show Notification.
- Open From Notification: Open From Notification.
- Created Date/Time: Time Created.
- Save in Public Storage: Save in Public Storage.
- Allow Cellular: Allow Cellular.
Android Teleguard Draft Messages
- Server ID: Server ID.
- Draft Text: Draft Text.
Android Teleguard Media
- Media Sent Date/Time: Create Date.
- Media Type: Media Type.
- TTL: TTL.
- Sender: Sender.
- ID: ID.
- Name: Name.
- Type: Type.
- Aspect Ratio: Aspect Ratio.
- Duration: Duration.
- Cache Name: Cache Name.
- Thumbnail Cache Name: Thumbnail Cache Name.
Android Teleguard Calls
- Call Date/Time: Timestamp.
- User Time: User Time.
- Type: Type.
- Sender: Sender.
- Receiver: Receiver.
- Content: Content.
- Status: Status.
- Is Successful: Content.
- Call Duration: Call Duration.
- Members Text: Members Text.
- Call Type: Call Type.
- Is Edited: Is Edited.
For more information or suggestions please contact: kalthoum.karkazan@forensafe.com
