Hacking Case Challenge Using the Full Version of ArtiFast Windows
02/02/2021 Tuesday
National Institute of Standards and Technology (NIST) provides DFIR challenges to help people learn about various types of challenges and the techniques that can be used to solve them. This challenge provides the following scenario. This challenge requires we analyze a drive disk image made available to us, to "Find any hacking software, evidence of their use, and any data that might have been generated".
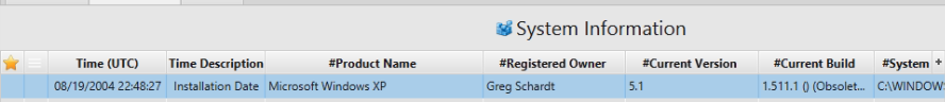
1. What operating system was used on the computer, when was the install date and what is the name of registered Owner?
Artifact: Computer Name.
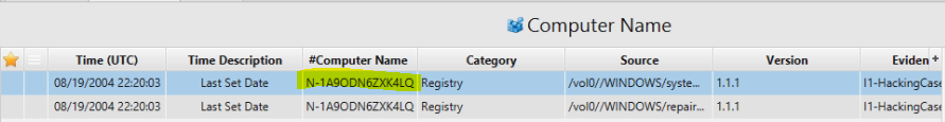
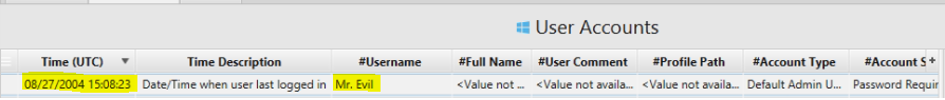
2. What is the computer account name?
Artifact: Computer Name same above in Time Description table.
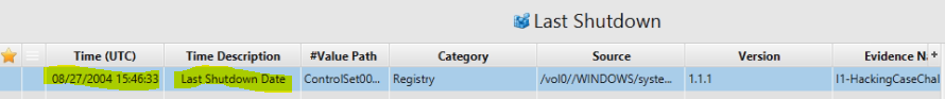
3. When was the last recorded computer shutdown date/time?
Artifact: Last Shutdown.
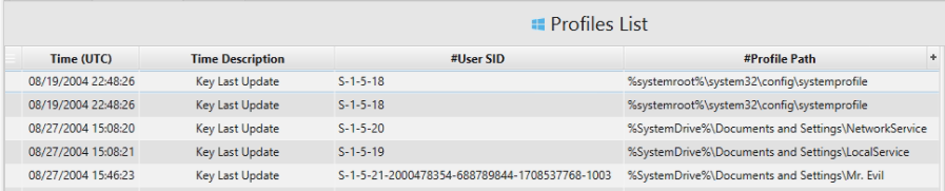
4. How many accounts are recorded (total number)?
Artifact: Profile List.
5. Who was the last user to logon to the computer?
Artifact: User Accounts.
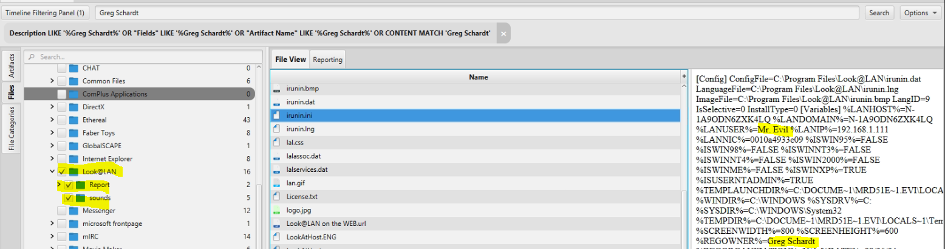
6. A search for the name of 'G=r=e=g S=c=h=a=r=d=t' (The equal signs are just to prevent web crawlers from indexing this name; there are no equal signs in the image files.) reveals multiple hits. One of these proves that G=r=e=g S=c=h=a=r=d=t is Mr. Evil and is also the administrator of this computer. What file is it? What software program does this file relate to?
Steps to Solve:
1. Go to file category.
2. Go to program file/Look@LAN folder.
3. Double click on irunin.ini file to see the content.
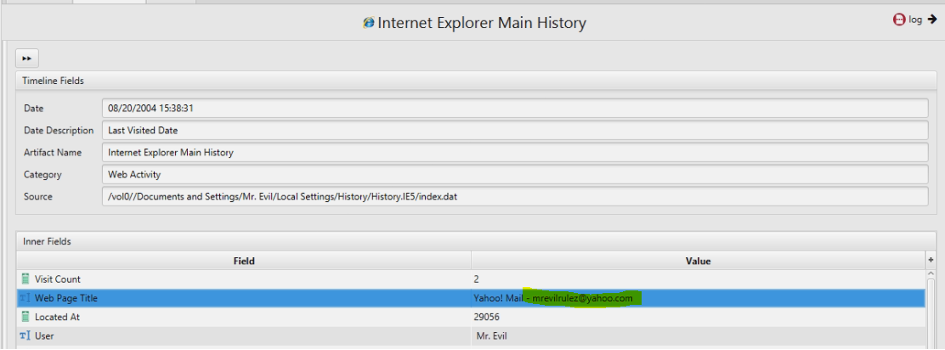
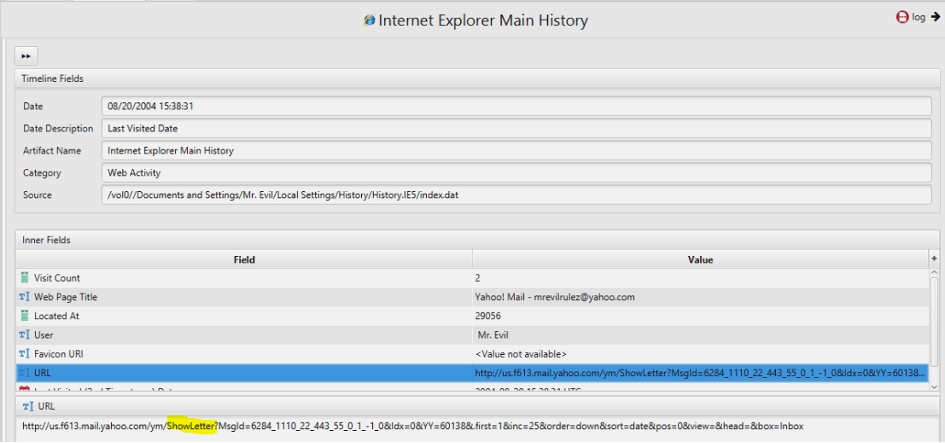
7. Search for the main user's web based email address. What is it?
Artifact: Internet Explorer Main History.
8. Yahoo mail, a popular web based email service, saves copies of the email under what file name?
Artifact: Internet Explorer Main History.
Answer: ShowLetter.
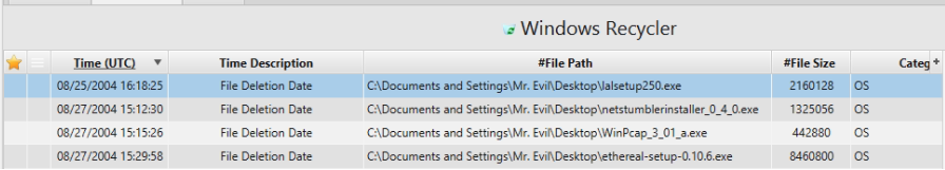
9. How many executable files are in the recycle bin?
Artifact: Recycle Bin.