Solving Magnet Virtual Summit 2025 CTF (Windows)
17/10/2025 Friday
The Magnet Capture The Flag event was held on February 13th as part of their Virtual Summit. The CTF questions were divided into four groups: iOS, Windows, Android & Ciphers. This challenge will be solved with ArtiFast (Full Version). This part will be related to the Windows challenge.
Artifacts Covered in this Challenge:
- Profiles List
- User Accounts
- Windows Event Logs (EVTX)
- Edge Chromium Downloads
- Games
- Edge Chromium History
- AmCache Application Programs
- PowerShell
- Windows OS Default Browser
- Windows Terminal
- Installed Programs
whoami? (5 points)
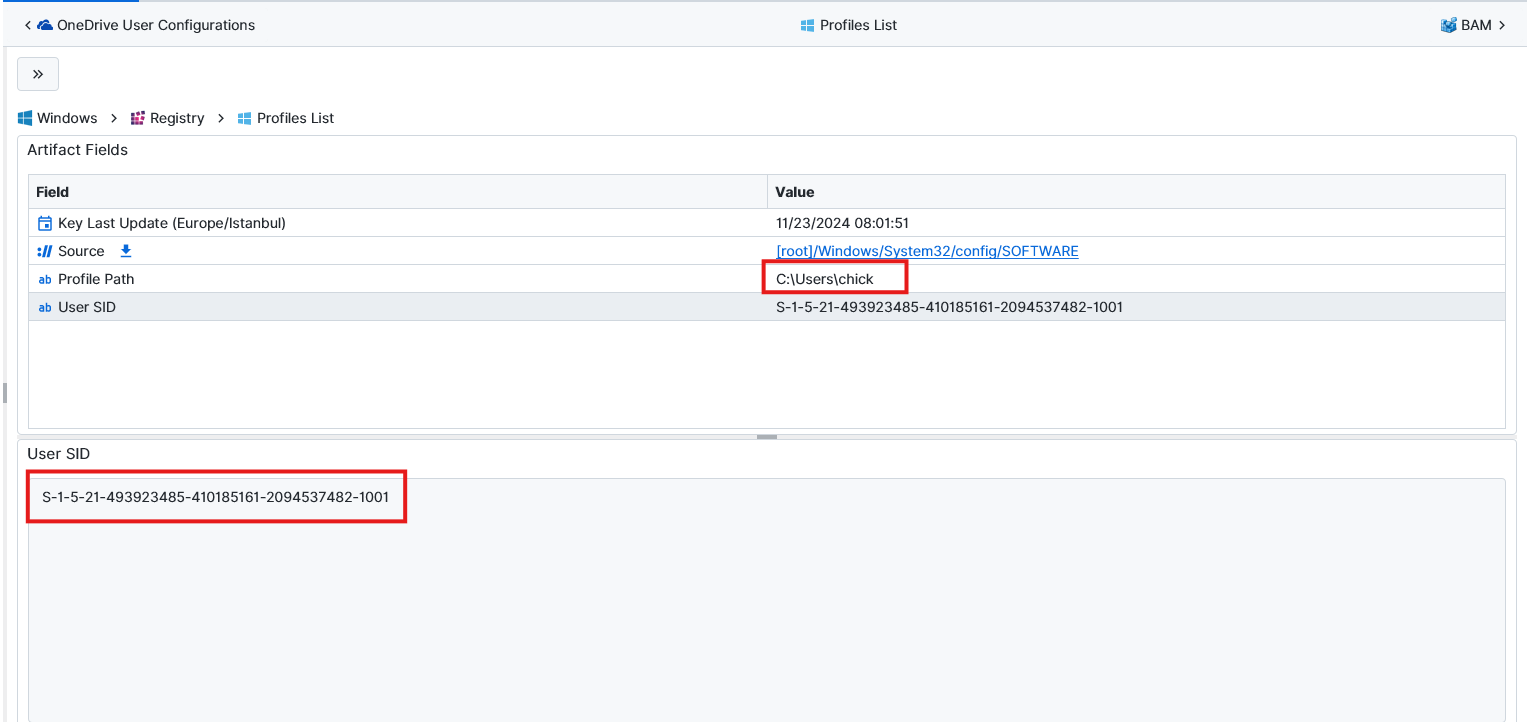
Q: What is the SID for the user "chick"?
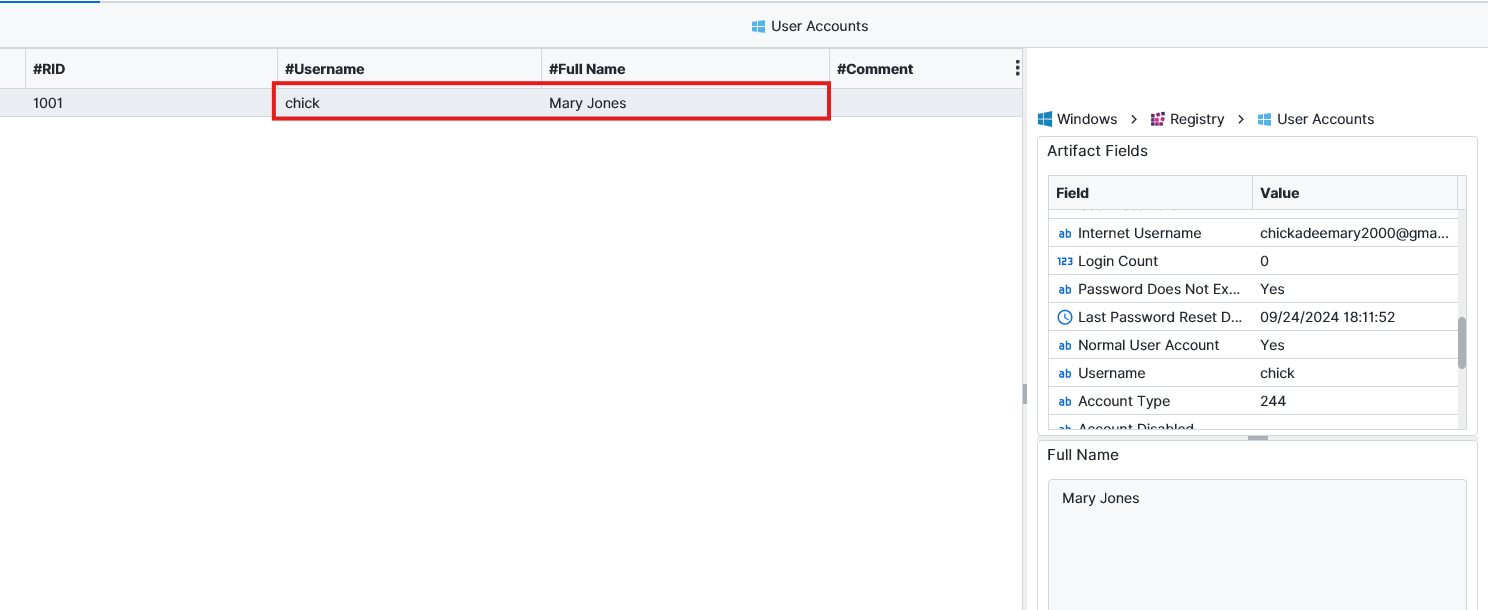
S-1-5-21-493923485-410185161-2094537482-1001. We can find the SID for “chick” user from Profiles List artifact under User SID attribute. We can also see that the full name of the user “chick” is Mary Jones from User Accounts artifact.
Goodbye! - 5 points
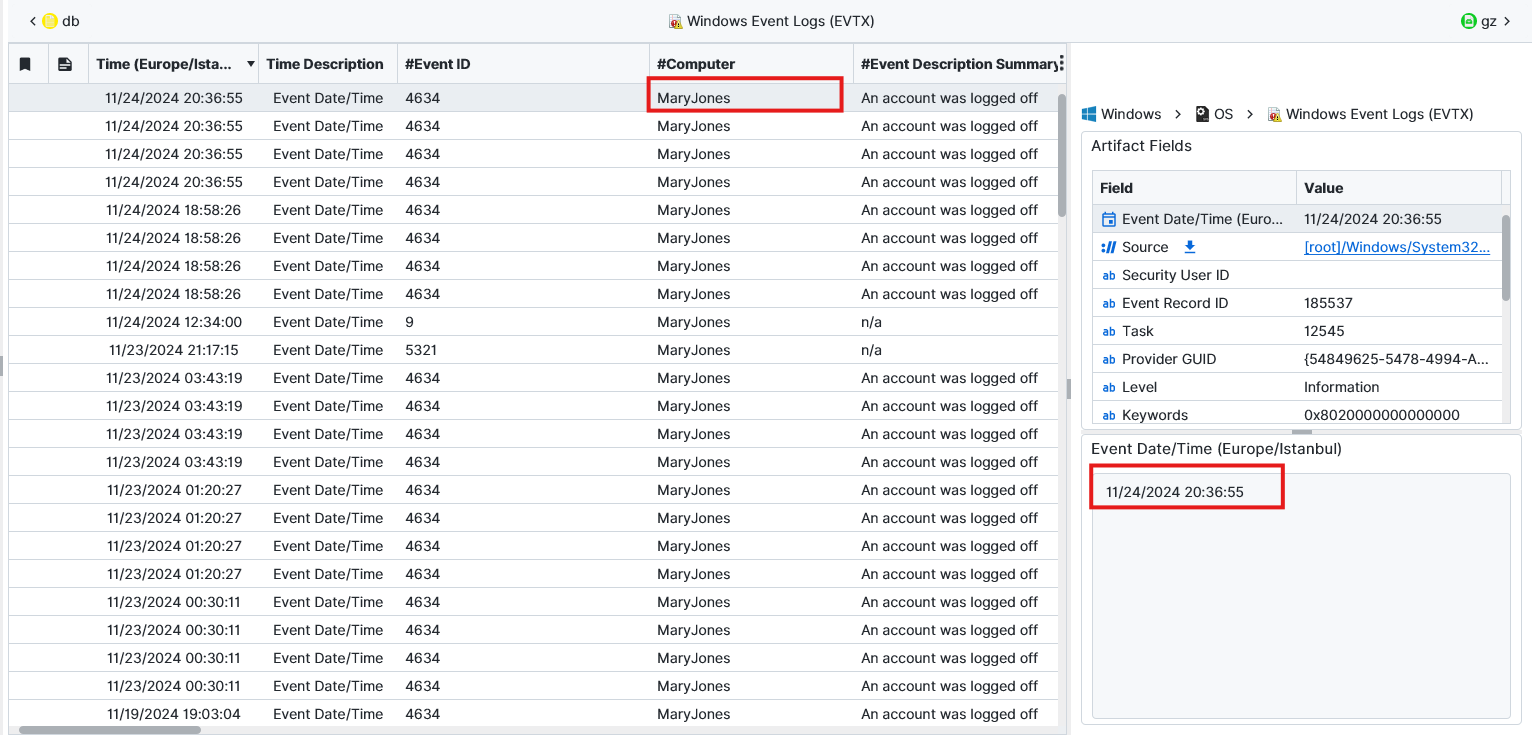
Question: When was the last logoff time for the user "chick"? (YYYY-MM-DD HH:MM:SS)
2024-11-24 17:36:55. We can see that the full name of the user “chick” is Mary Jones from User Accounts artifact. Then we want to filter on event ID 4634 to show the log off times. Then when we sort by the time we will see that the last log off was from 11/24/2024 20:36:55 (Europe/Istanbul) or 11/24/2024 17:36:55 UTC.
In the Zone - 5 points
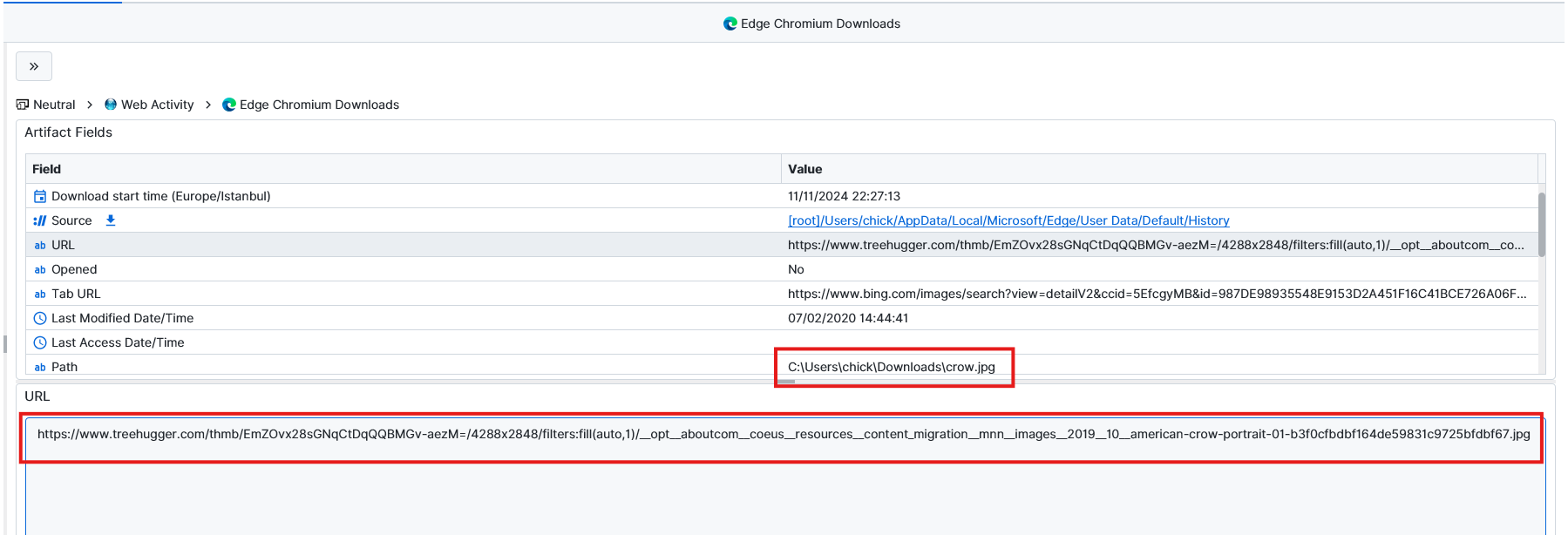
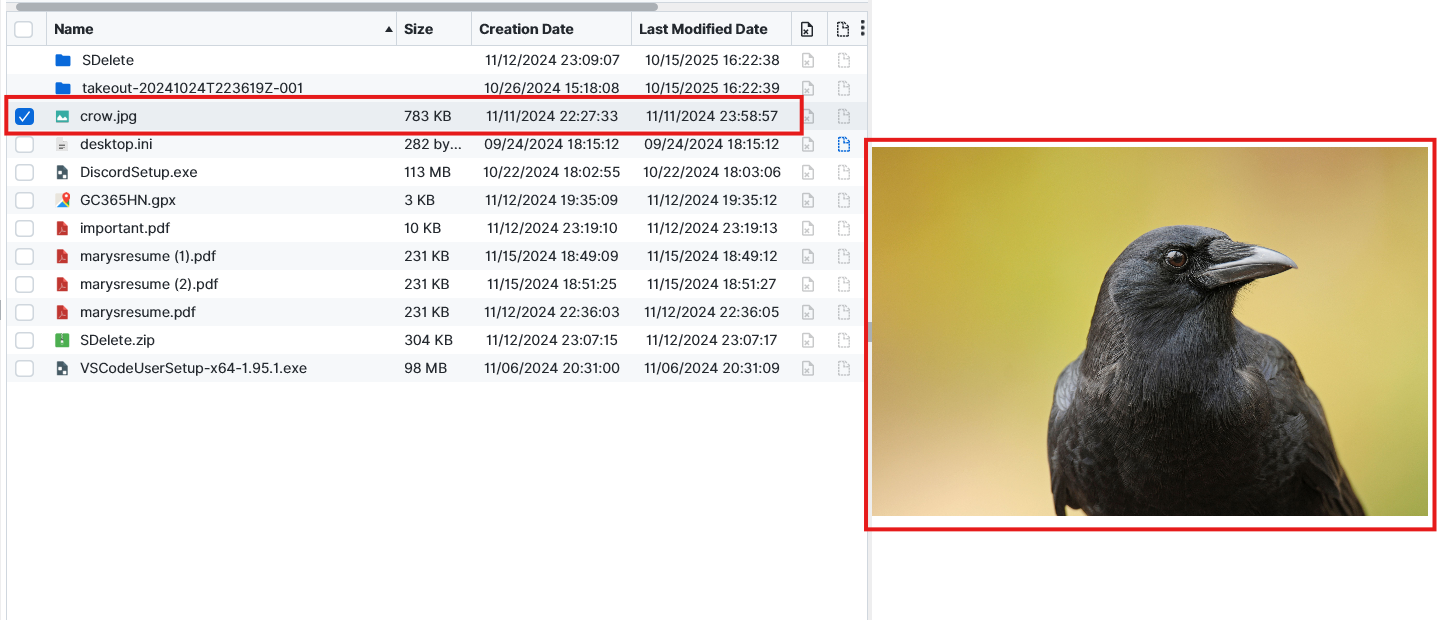
Question: What is the host URL that crow.jpg was downloaded from?
https://www.treehugger.com/thmb/EmZOvx28sGNqCtDqQQBMGv-aezM=/4288x2848/filters:fill(auto,1)/__opt__aboutcom__coeus__resources__content_migration__mnn__images__2019__10__american-crow-portrait-01-b3f0cfbdbf164de59831c9725bfdbf67.jpg. The answer to this question was inside the Edge Chromium Downloads, which shows the image name and the URL that was downloaded from.
Sweet Find - 5 points
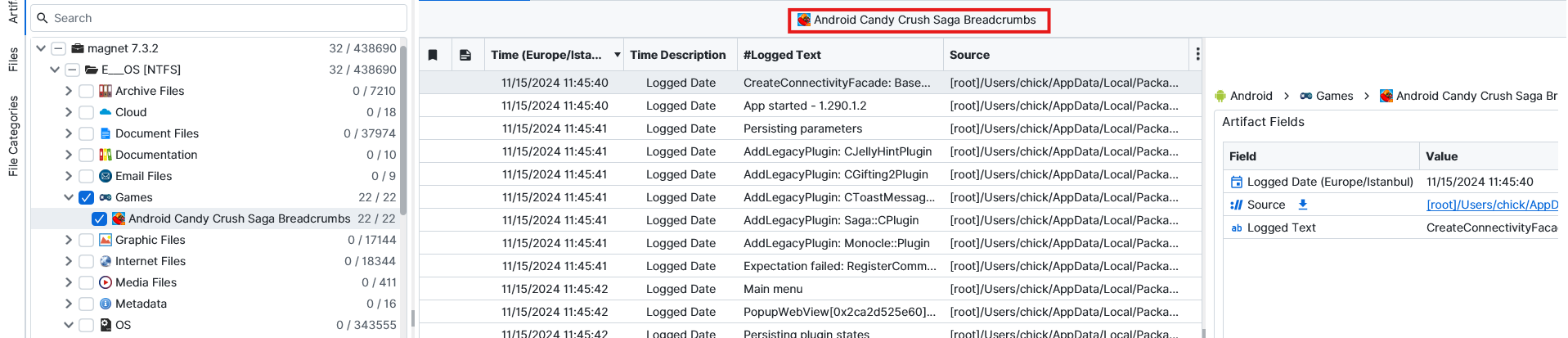
Question: What popular game was installed on the computer?
Candy Crush Saga. This one was pretty simple. Artifast shows installed games on the computer via Games artifact,
Buried Treasure - 5 points
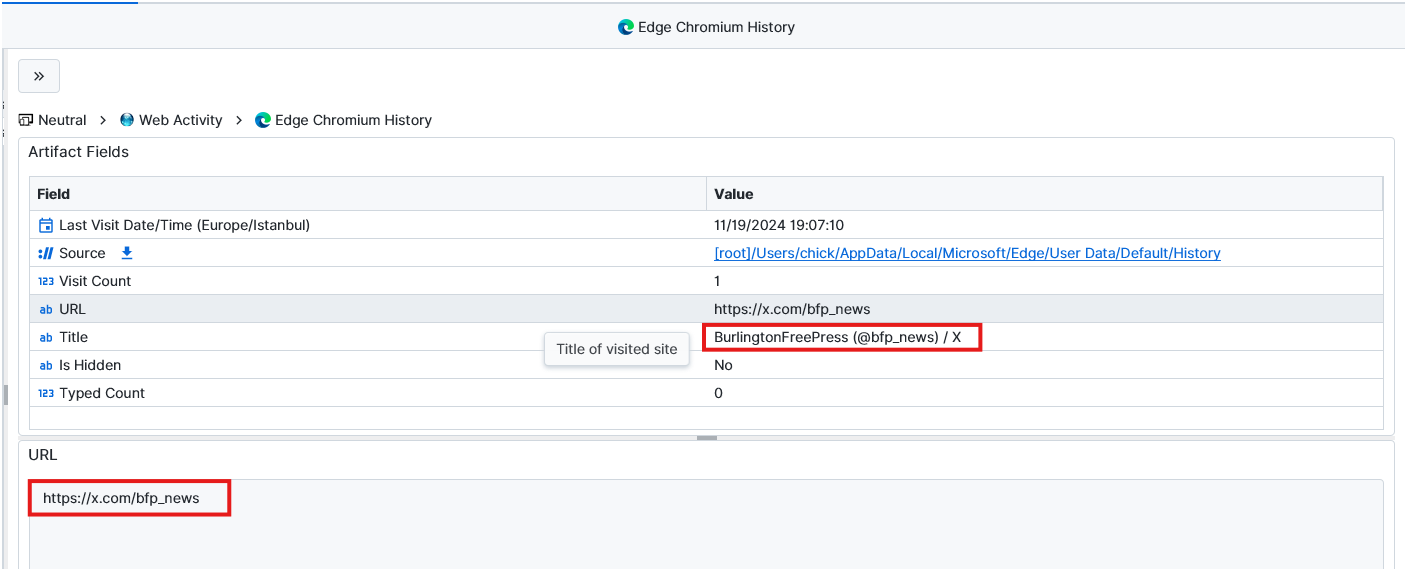
Question: On what social media platform did Mary look at a Burlington news account?
X. After searching for Burlington we found from Edge Chromium History the link of the used website for it which is X.
Follow the Thread - 5 points
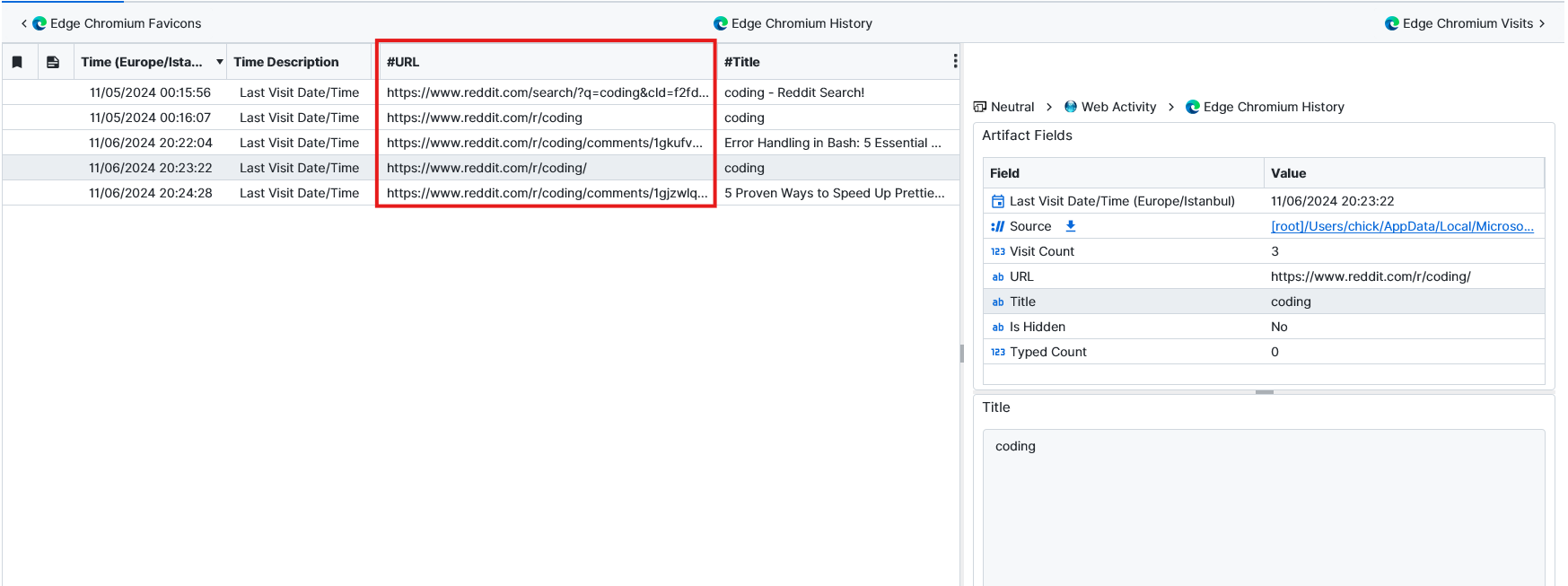
Question: Where did Mary look for help with her coding questions?
Reddit. It would make sense to look for help on the internet. After searching a bit, we found the answer from Edge Chromium History that she was using Reddit.
Venomous Variables - 5 points
Question: What language was Mary's first program written in?
Python. The answer to this question could be found in a couple of artifacts. This time we used AmCache Application Programs, and we could see python there as the only programming language.
We could also see from the file system at root/Users/chick that there is an import random.py file.
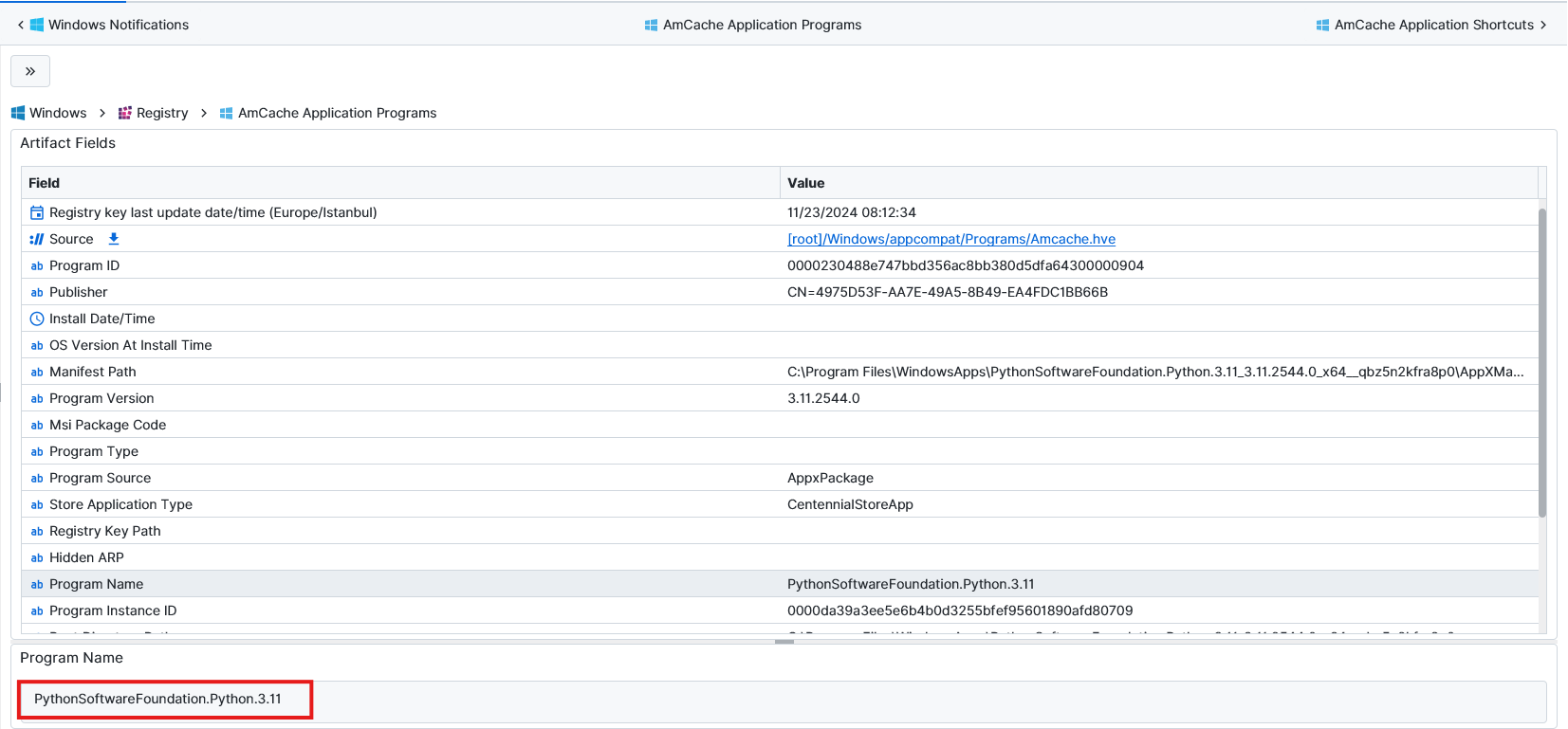
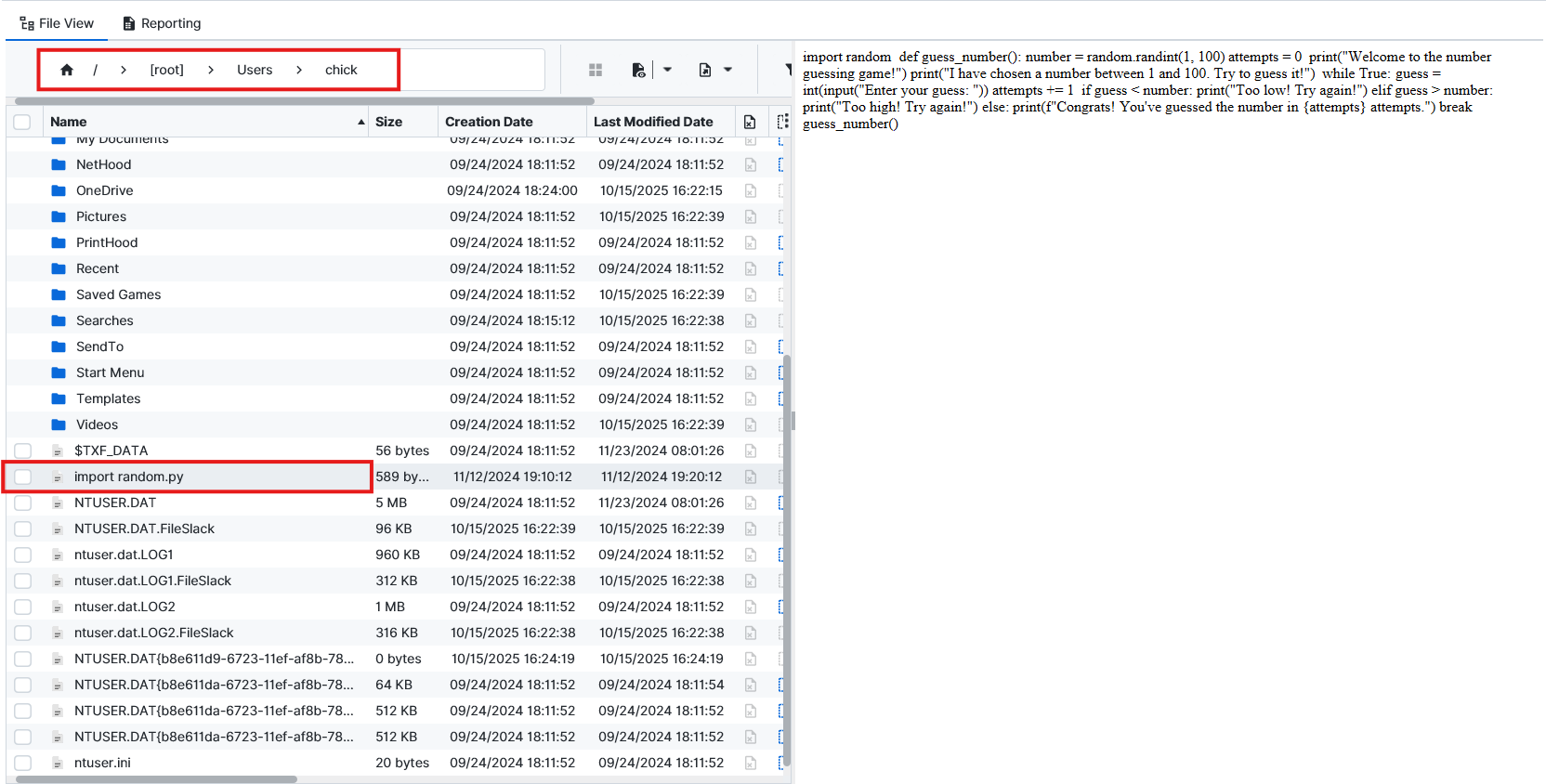
Account Registration - 10 points
Question: What is the creation date for Mary’s user account? (YYYY-MM-DD HH:MM:SS)
09/24/2024 18:11:51 (Europe/Istanbul) or 09/24/2024 15:11:51 UTC. From the Windows Event Logs, if we look for Event ID 4720, which is accounts creating ID, we could see the time of creation of the account for Mary.
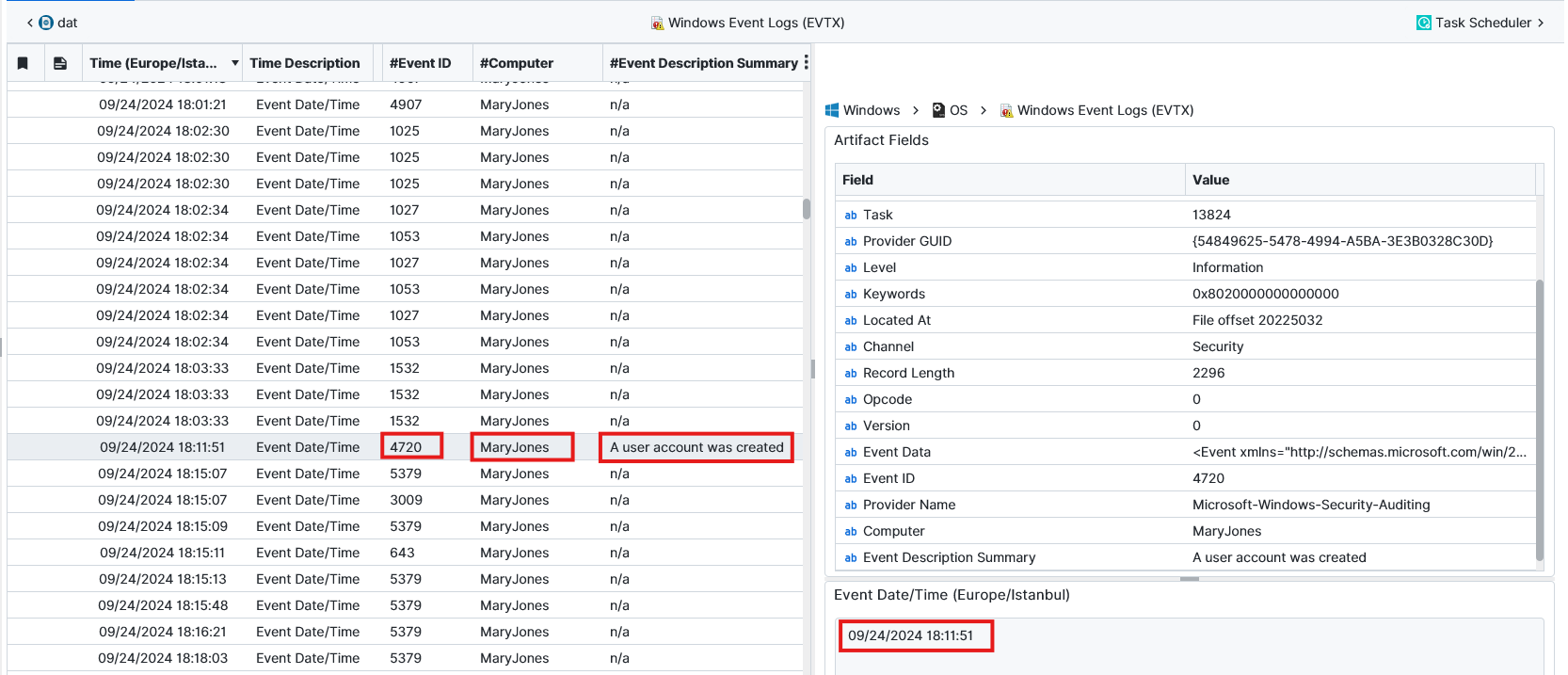
It's History Now - 10 points
Question: What was the name of the geocache that was completed?
Something's Fishy. After searching for geocache we found a link inside the Edge Chromium History artifact. From the title we can see the name of the geocache. Also if we go to the URL provided by the artifact the answer is there as well.
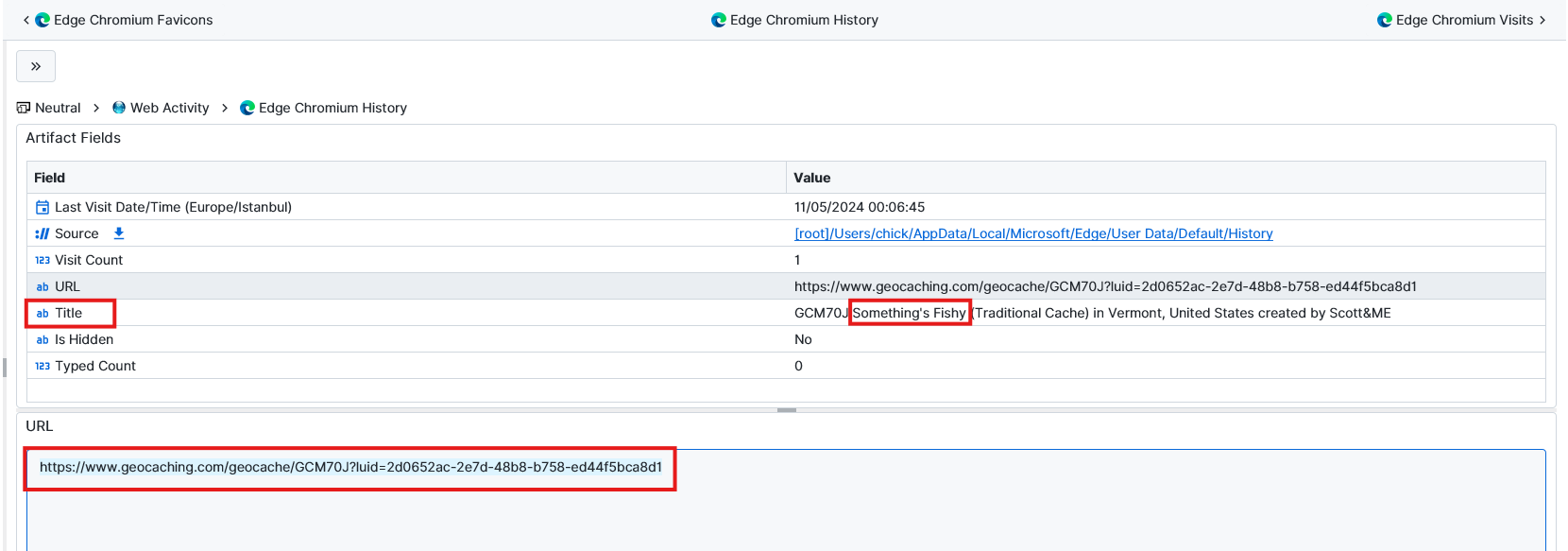
Where did it go? - 10 points
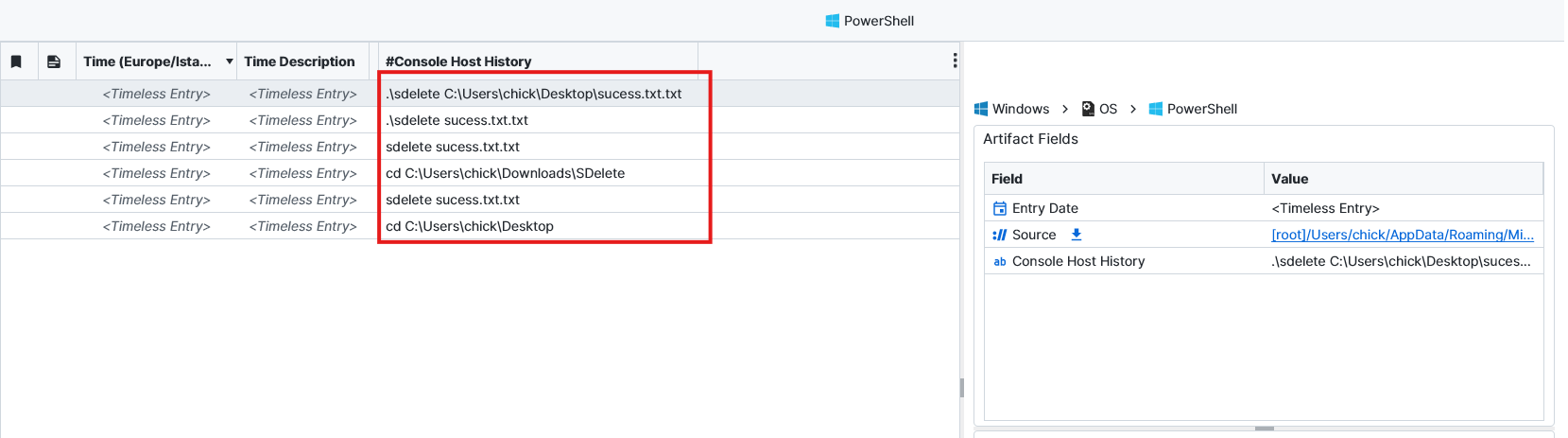
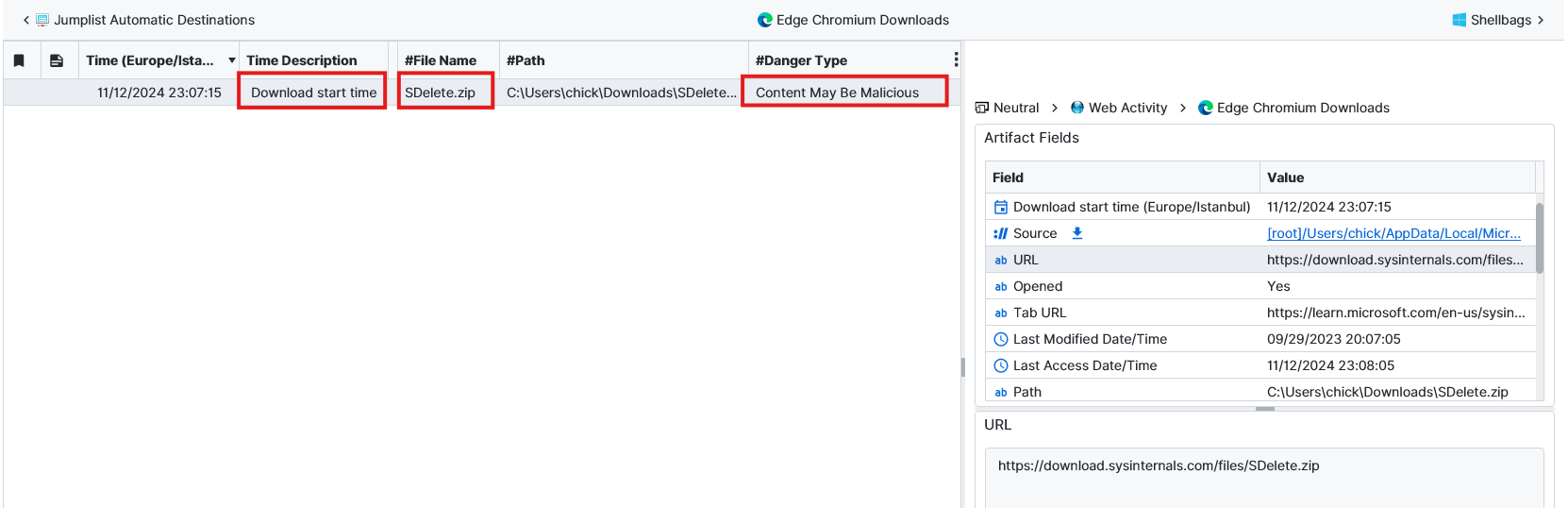
Question: What file was an anti-forensics tool used on?
SDelete. After checking the PowerShell artifact to see console history we could see many SDelete usages which were used to delete success.txt. When we dig more we can see that SDelete was downloaded from Edge using Edge chromium Downloads with a malicious tag.
Used by only the PROs - 10 points
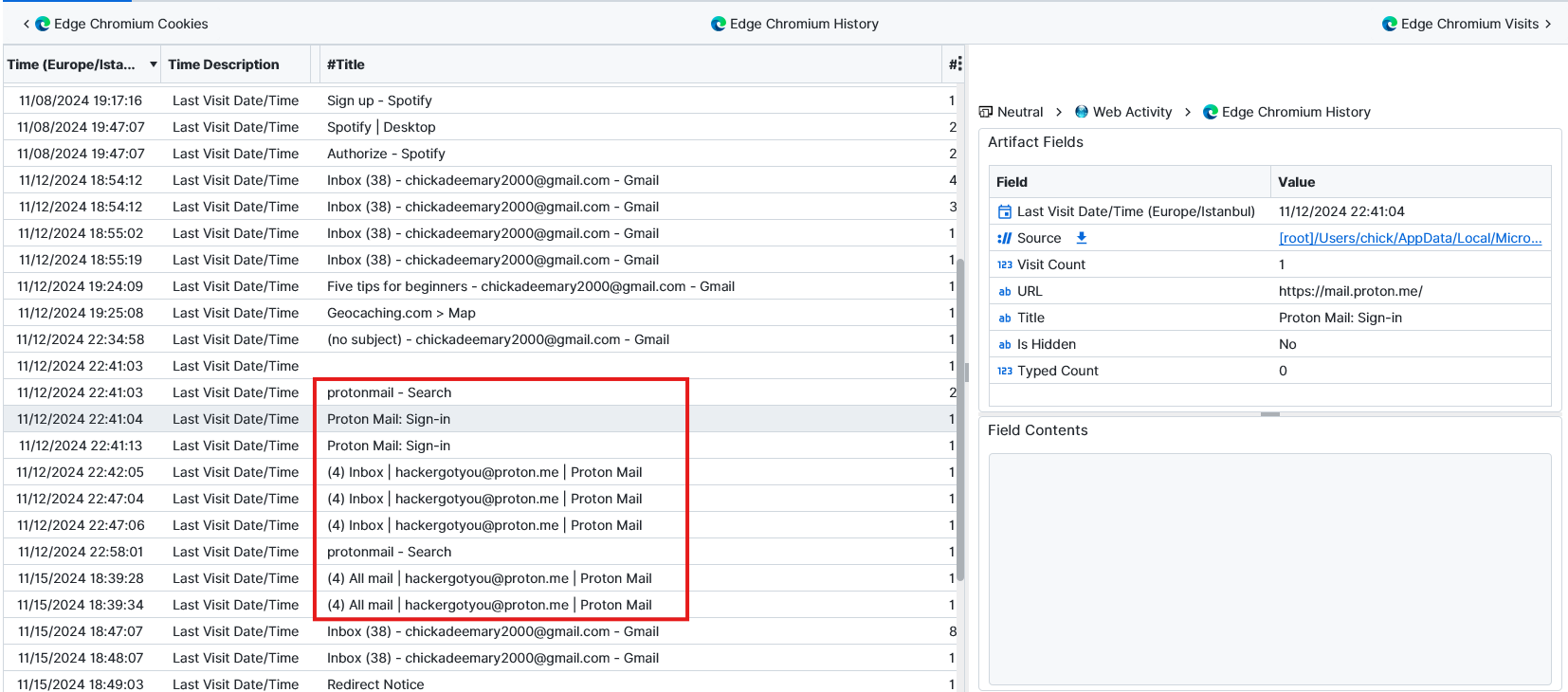
Question: What email service is Mary using other than gmail?
Proton Mail. When we look for mails from Edge Chromium History we could spot Proton Mail and Gmail that the user was using.
If you don't choose, I'll choose for you - 10 points
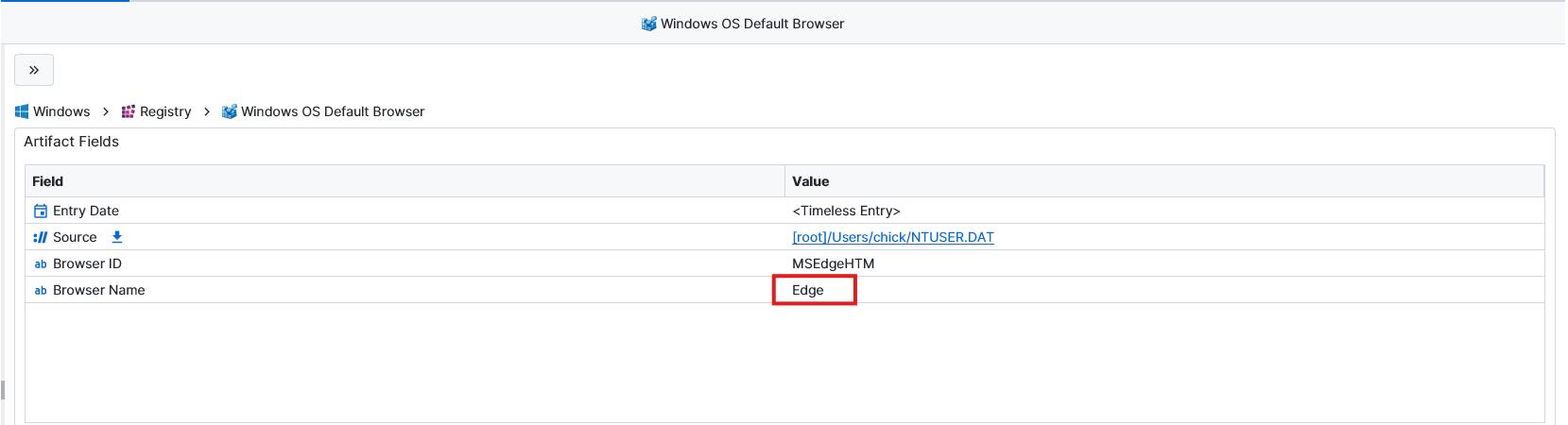
Question: What is the default browser set as?
Edge. This one was also pretty simple. Artifast has an artifact called Windows OS Default Browser.
A Stamped Link - 25 points
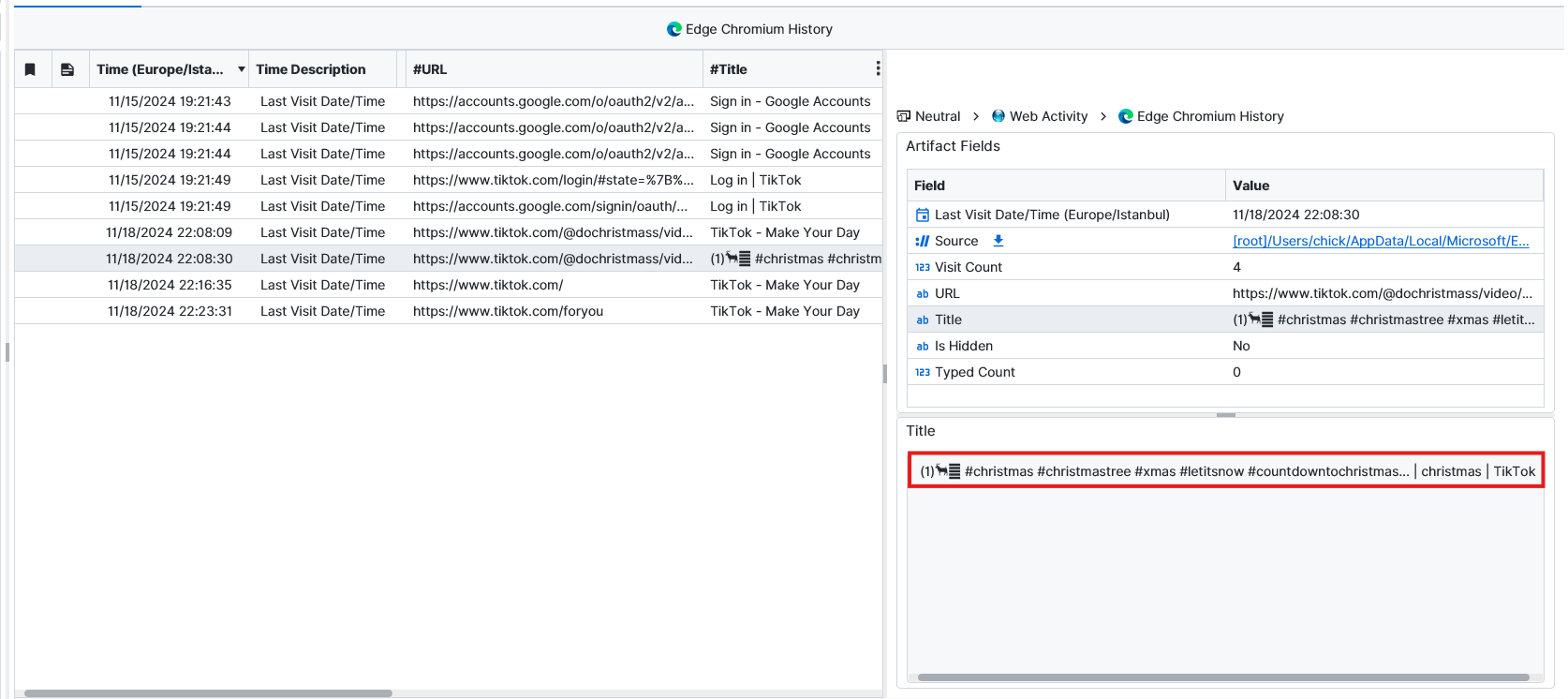
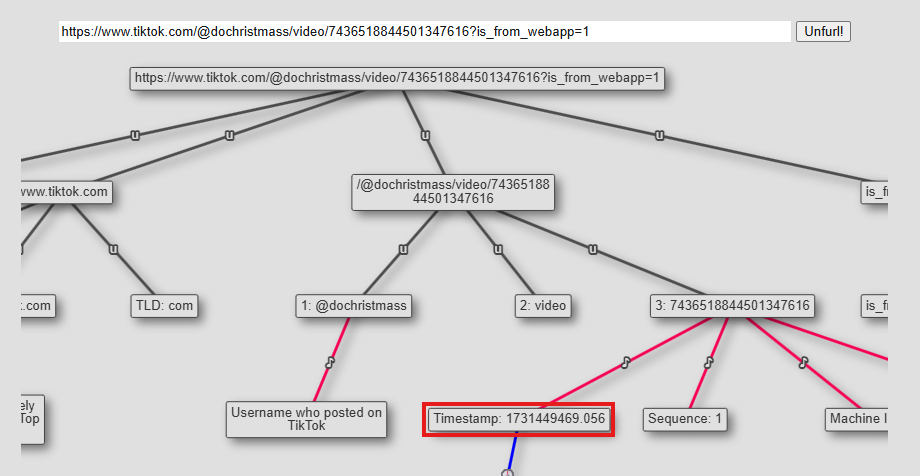
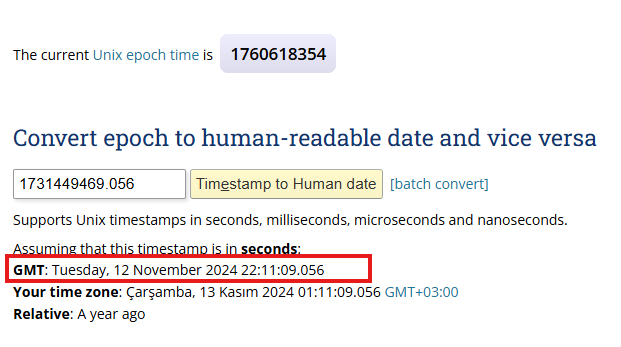
Question: What time was the tiktok that Mary watched posted? (YYYY-MM-DD HH:MM:SS UTC)
2024-11-12 22:11:09. When we look for TikTok Edge Chromium History shows us some visited links from tiktok. There is only one link that’s related to a watched content from TikTok. We can use Unfurl.com to check the timestamp of the video using the link provided by Artifast. After taking the timestamp we can convert it to UTC time to find the answer. For this we used epochconverter.com website.
Unravel the Mystery - 25 points
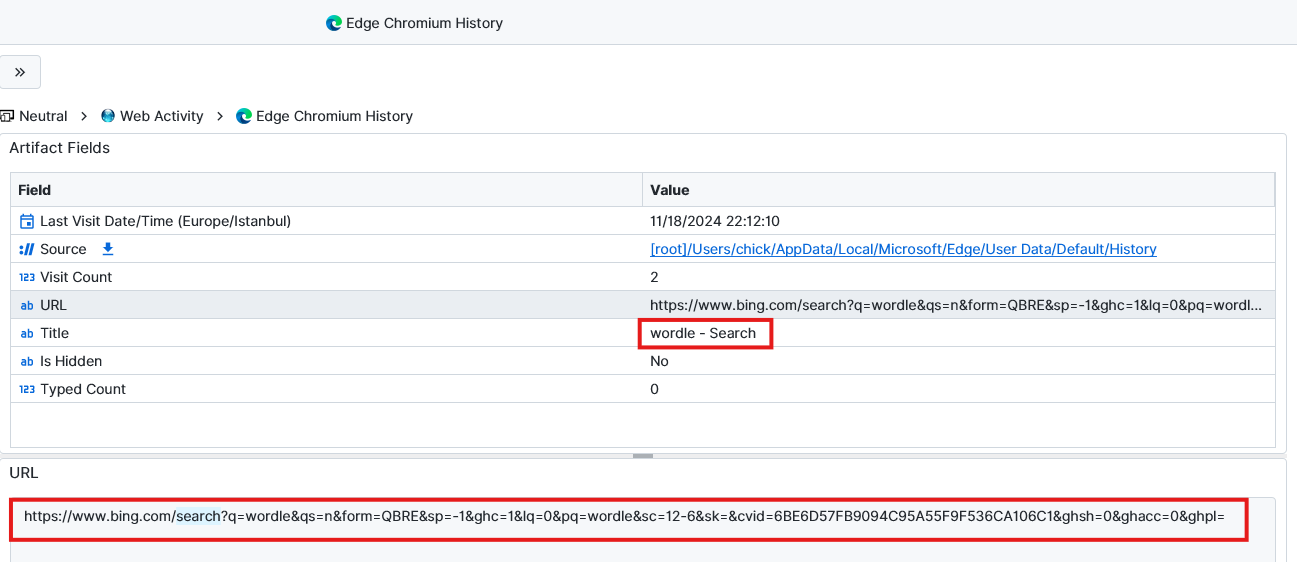
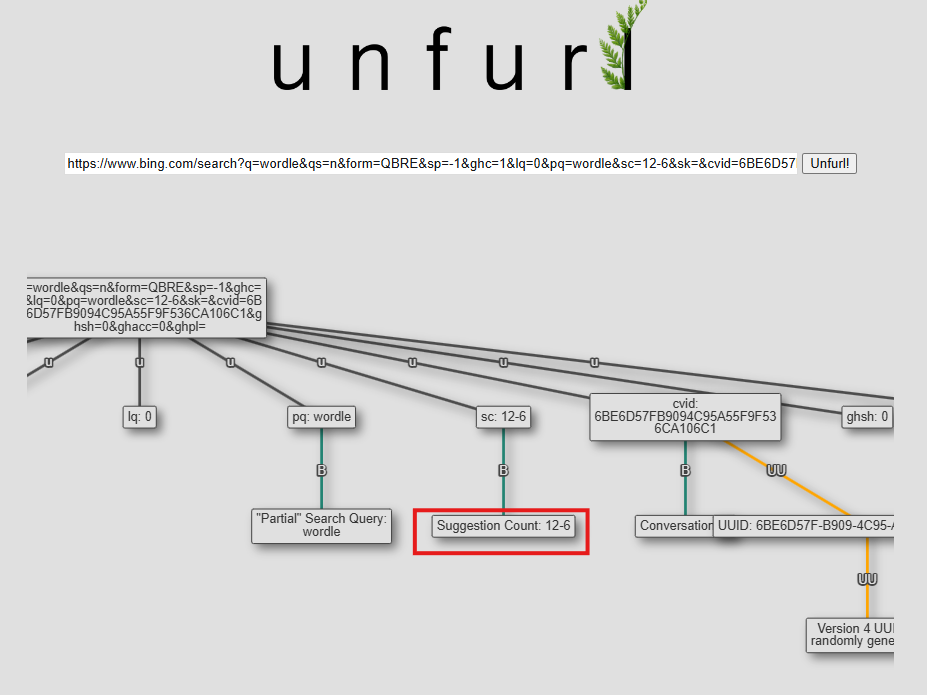
Question: What was the suggestion count when Mary was going to play a popular word-based browser game?
12-6. Since the only game that was on computer was Candy Crush, this should be a game accessed by browser. When we look at the web history using Edge Chromium History, we notice Wordle website has been accessed. We can use Unfurl.com again to check the count.
Login Credentials Required - 25 points
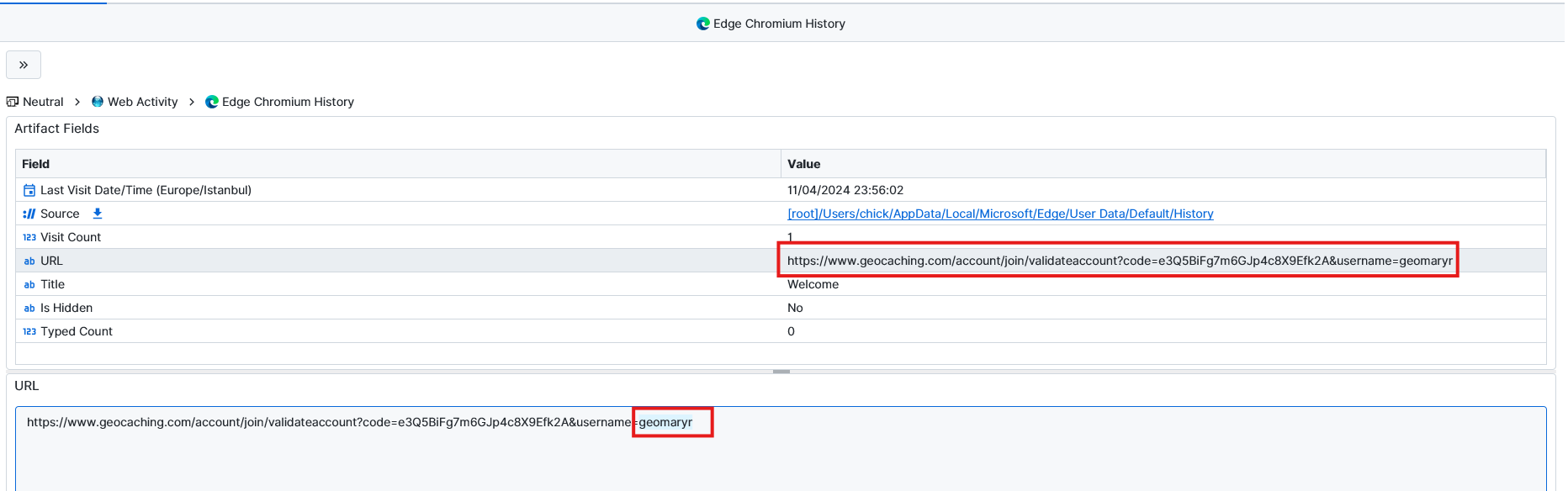
Question: What is Mary’s username on geocaching.com?
geomaryr. If we check the Edge Chromium History artifact and filter by geocaching.com we notice a link with account validation, which shows the username of the account
A Shadow of the Real Thing - 25 points
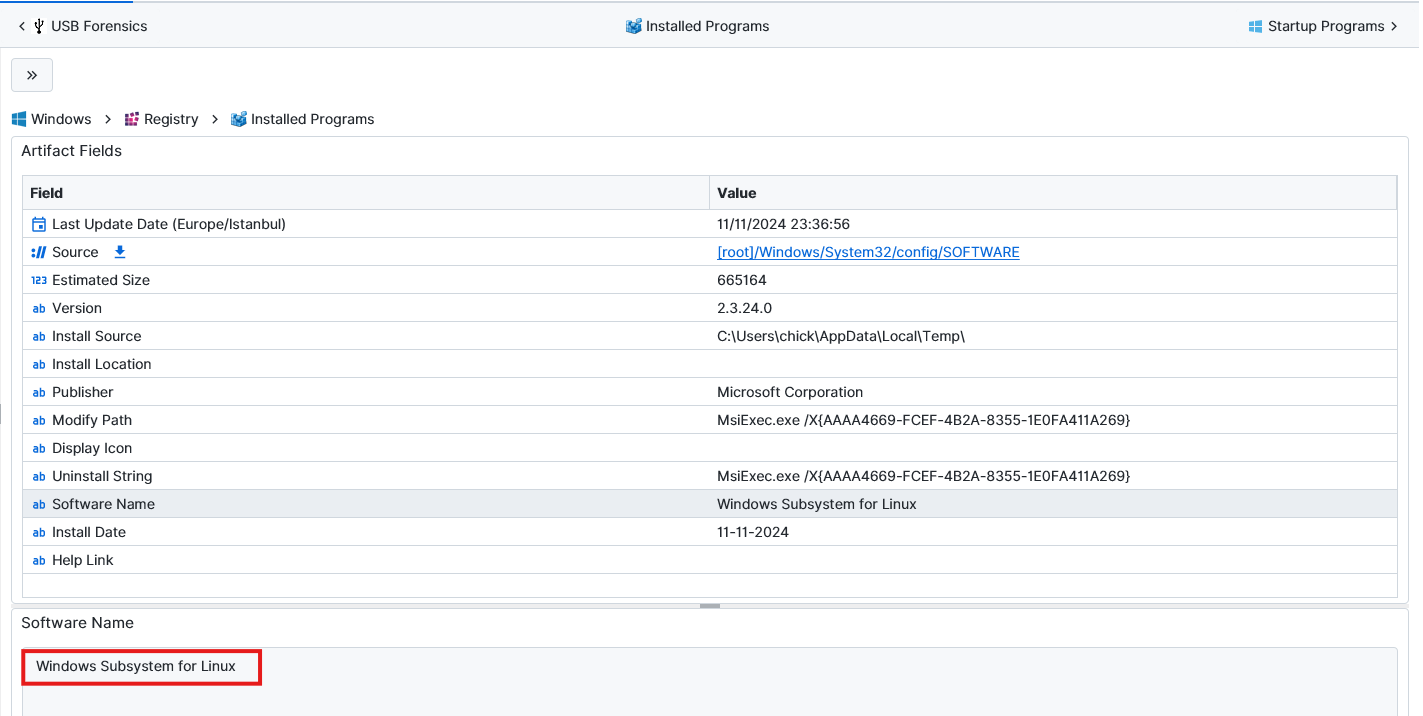
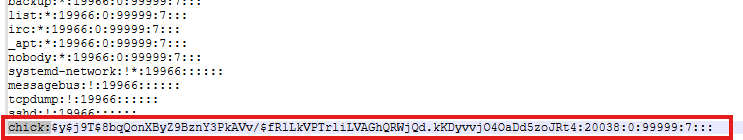
Question: What is the hashed password for the user "chick"?
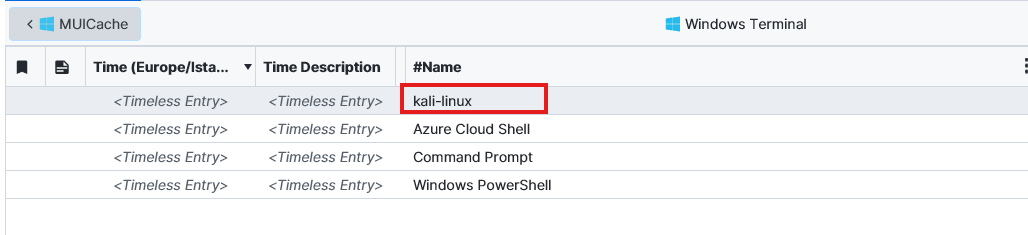
$fRlLkVPTrliLVAGhQRWjQd.kKDyvvjO4OaDd5zoJRt4. After searching for a while, we notice that inside the Windows Terminal artifact, there is kali-linux, which gives a hint. This means Kali was installed on the Windows subsystem. To confirm this we check the Installed Programs artifact and we can see it there. Now we just need to locate it. After filtering the word “Kali” on the file system we managed to find the vhdx where the data is stored.
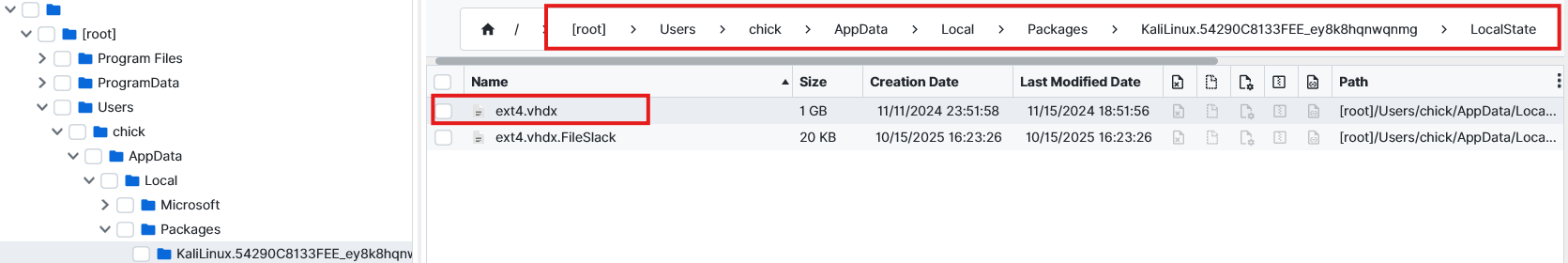
After exporting it we could analyze it. I used Notepad++ and searched for the word “chick” then managed to find the hashed password.
I rate it 4 out of 10 - 25 points
Question: What was the username of the person who saw the clouds coming in at 6:30 while doing a geocache?
wandering4cache. There is a downloaded file from geocache website inside Edge Chromium Downloads artifact which is located at C:\Users\chick\Downloads\GC365HN.gpx.
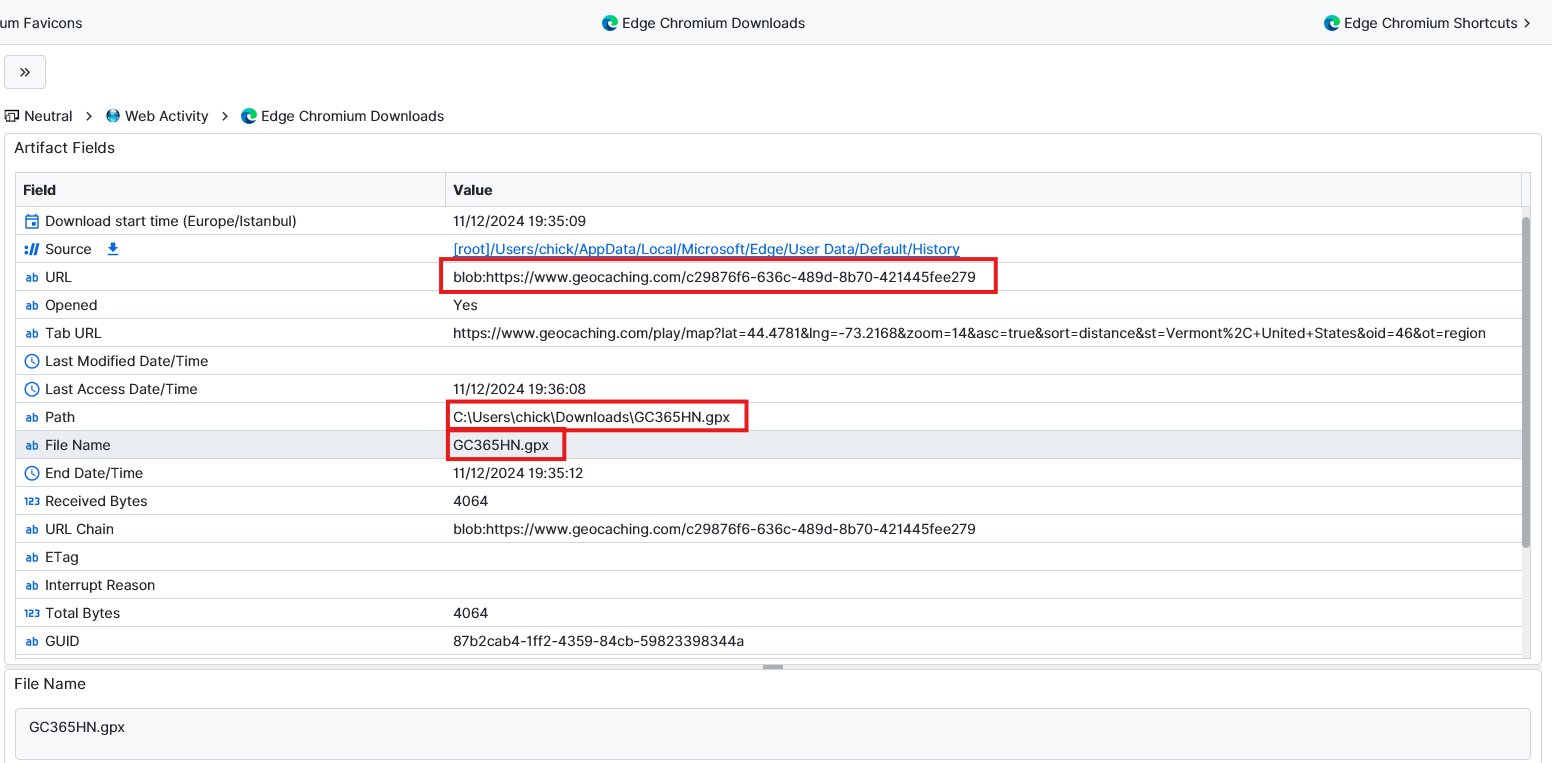
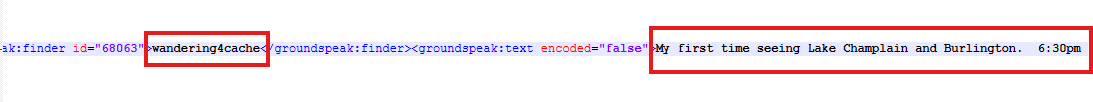
When we found the file on the file system, we could see what was inside the GC365HN.gpx. There was a note saying “My first time seeing Lake Champlain and Burlington. 6:30pm clouds" and before that, there is the username of the person.
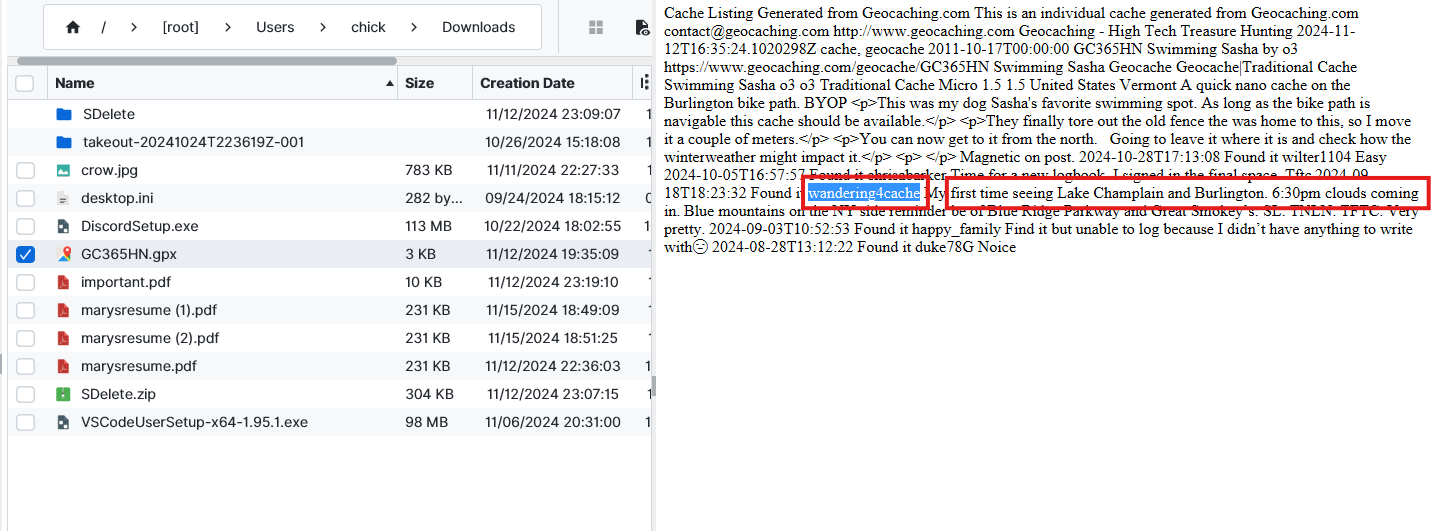
Out of the Ordinary - 50 points
Question: What suspicious command line tool was installed on Mary’s system?
Steghide. We could not find anything similar to this on the Windows other than SDelete, but that was not installed on the system. Since we know there is a Kali installed via Windows Subsystem, we can check the hard disk of the virtual machine that we extracted earlier. From the disk, since it’s Linux we can check dpkg.log which is Debian Package Management, located at Ext4.vhdx > [root]\var\log\dpkg.log using FTK Imager. There we see the steghide program has been installed on the system. Steghide isa steganography program that is able to hide data in various kinds of image and audio files.
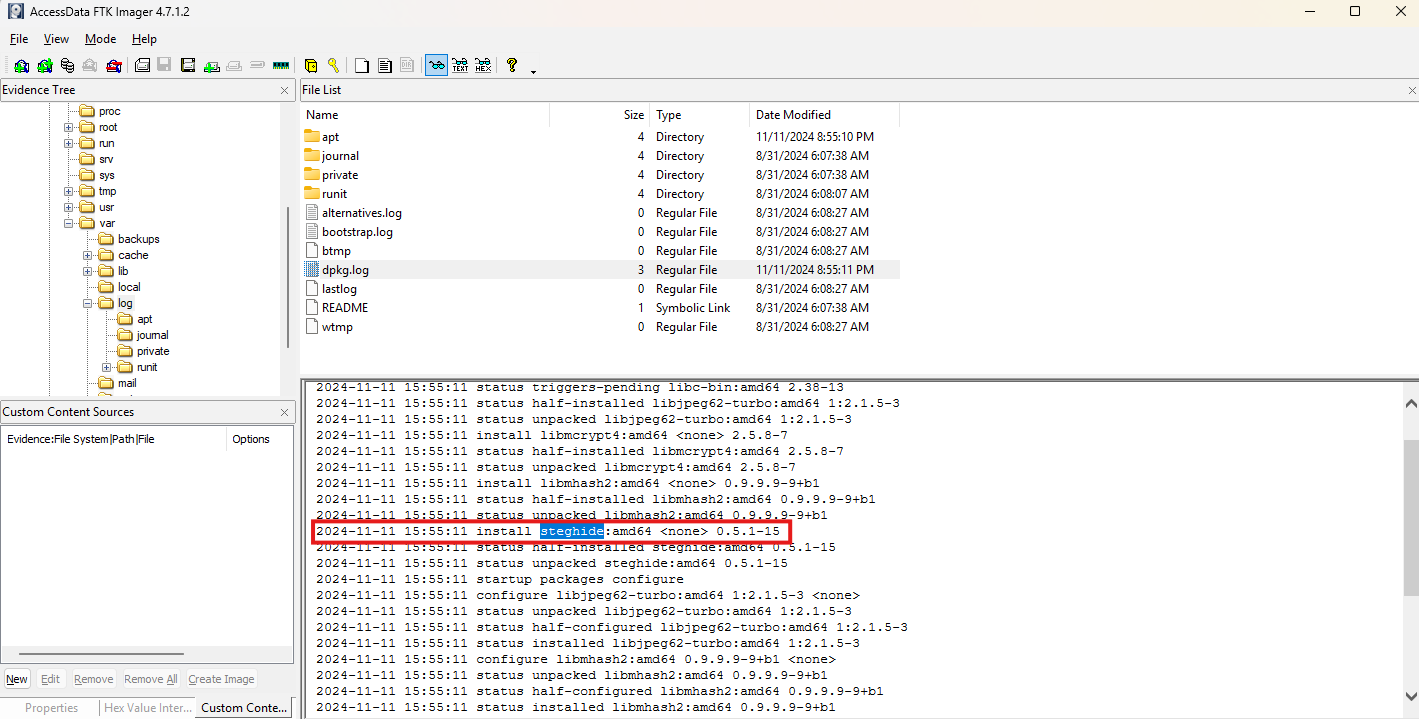
DAdataTA - 75 points
Question: What does the file sucess.txt.txt contain?
Steghide. Since SDelete was used to delete this file we can not trace it on the windows. However, we can still check inside the Linux VHDX since we know steghide was installed there to maybe hide something.
We can check the user console history, which is located at Ext4.vhdx > [root]\home\chick\.bash_history.
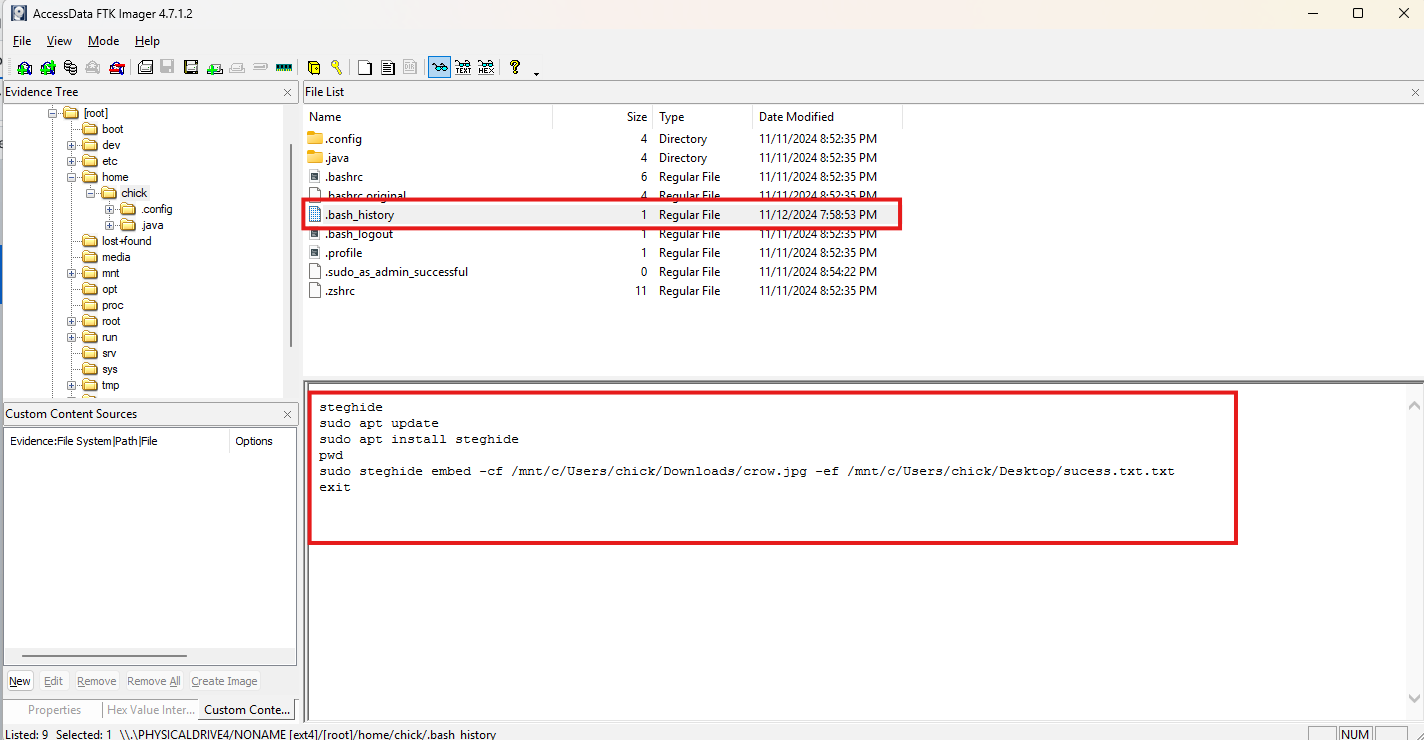
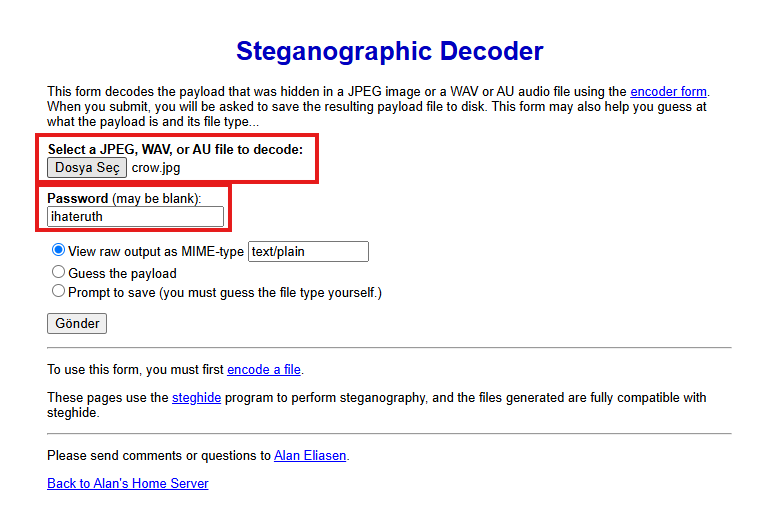
There we see that Steghide was used to hide the content of the secret.txt.txt file inside the crow.jpg. We still need to decode it with a password to see what was inside.
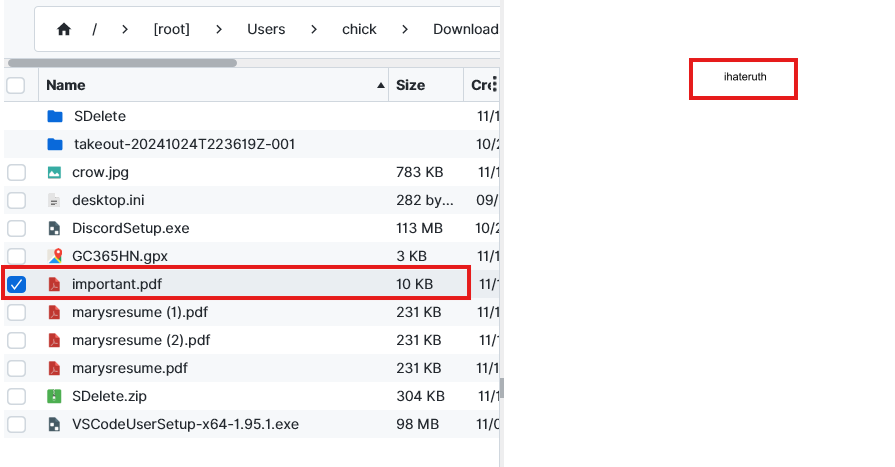
There is a PDF in the downloads folder with the name important.pdf, which looks interesting. After checking its content we can find the password in plain text “ihateruth”.
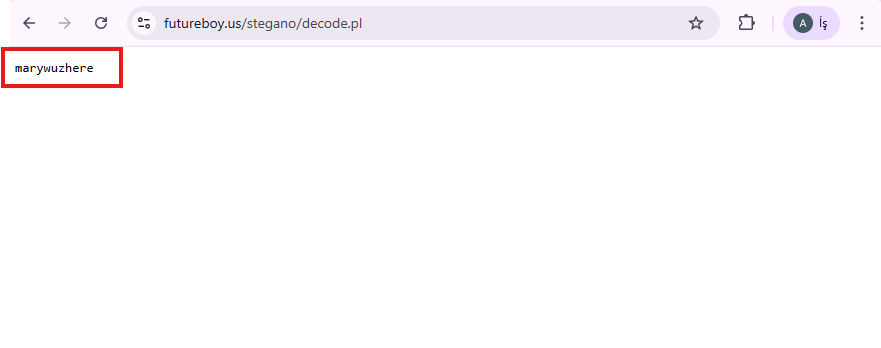
to decode the picture from futureboy.us website. There we go, “marywuzhere” was inside the sucess.txt.txt file.
×
