Investigating iOS MEGA
13/06/2025 Friday
MEGA is a cross-platform file hosting and sharing service that can be accessed through web browsers and dedicated apps for various operating systems. This application emphasizes end-to-end encryption to protect user data. It provides an alternative to well-known cloud storage services like Google Drive and OneDrive. The iOS version allows users to store, share, and access their files securely from their mobile devices.
Digital Forensics Values of iOS MEGA
Forensic investigators can gather valuable information from locally stored artifacts, as demonstrated below. These parsers can collect and display details about MEGA accounts and the activities performed using them. These findings can help reconstruct a user’s actions, file transfers, and potential collaborations with others.
Location of iOS MEGA
iOS MEGA artifact can be found at the following location:
private/var/mobile/Containers/Data/Application/<App-GUID>/Library/Application Support/karere-.db
Analyzing iOS MEGA Artifacts with ArtiFast
This section will discuss how to use ArtiFast to extract iOS MEGA artifacts from iOS machines’ files and what kind of digital forensics insights we can gain from the artifact.
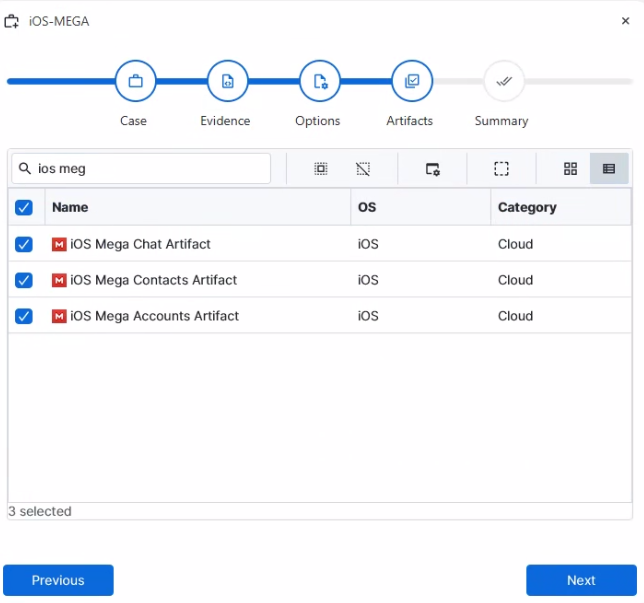
After you have created your case and added evidence for the investigation, at the Artifact Selection phase, you can select iOS Mega artifact parsers:
×
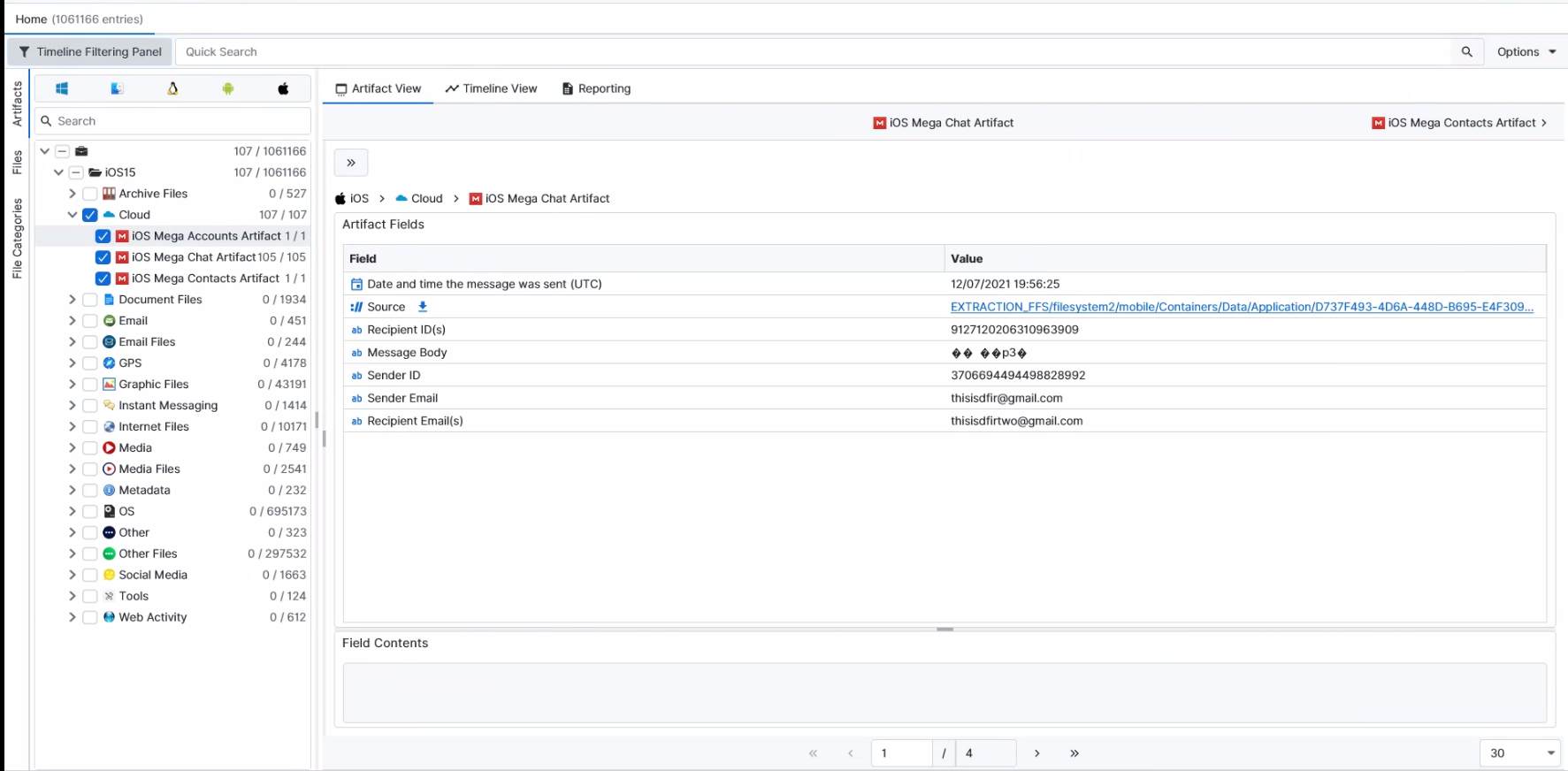
Once ArtiFast parsers plugins complete processing the artifact for analysis, it can be reviewed via “Artifact View” or “Timeline View,” with indexing, filtering, and searching capabilities. Below is a detailed description of iOS Mega artifacts in ArtiFast.
iOS Mega Text Messages
- Message Content : The content of this message.
- Message Sent Date/Time : Message Sending Date/Time.
- Sender Email : Email of the message sender.
- Sender ID : The ID of the message sender.
- Receiver Email : Email/s of the message receiver/s.
- Chat ID :The chat ID.
iOS Mega Accounts
- User ID : The user ID.
- First Name : IThis user's first name.
- Last Name : This user's last name.
- Email Address : The email address of this account holder.
iOS Mega Contacts
- User ID : The user ID.
- First Name : This user's first name.
- Last Name : This user's last name.
- Email Address : The email address of this account holder.
For more information or suggestions please contact: ekrma.elnour@forensafe.com
