Investigating Signal with ArtiFast Signal
07/11/2025 Friday
Signal is a cross-platform messaging application which enables users to send and receive one-to-one and group messages including texts, voice notes, files, photos, videos, and make voice and video calls. Signal was released initially in July 2014 and has become one of the most popular instant messaging applications due to the security and privacy it offers to the users. Many security-conscious users and even government officials are using the application as a form of secure communication channel.
The platform supports end-to-end encrypted communication. What makes Signal different from other social media platforms is that the messages and attachments (in Android) are stored encrypted. Signal databases are encrypted with different versions of SQLCipher depending on the operating system. To be able to decrypt Signal database, a full file system acquisition of the mobile device should be performed. In addition to the full file system acquisition, the keys related to Signal should be extracted from Android Keystore/iOS Keychain.
Digital Forensics Value of Signal Artifacts
Encrypted instant messaging applications are safeguarding users’ online presence by providing security and privacy; however, these applications create a challenge for digital forensics investigators as criminals are also benefiting from the provided security to hide their digital footprint and limit data retrieved by examiners. The analysis of the encrypted communication plays a key role in uncovering criminal activity. Therefore, Forensafe ArtiFast team decided to release a free version with fully functional Signal artifact parsers for Android, iOS and Windows.
Structure and Location of Signal Artifacts
The majority of Signal artifacts are maintained within SQLite database files, each containing multiple tables with information regarding users’ actions on the application. Signal artifacts are found at the following locations:
Android
- /data/user/{User Number}/org.thoughtcrime.securesms/databases/signal.db
- /data/user/{User Number}/org.thoughtcrime.securesms/app_parts/
- /data/user/{User Number}/org.thoughtcrime.securesms/shared_prefs/org.thoughtcrime.securesms_preferences.xml
iOS
- private/var/mobile/Containers/Shared/AppGroup/{App_GUID}/grdb/signal.sqlite
- private/var/mobile/Containers/Shared/AppGroup/{App_GUID}/Attachments/
Windows
- AppData\Roaming\Signal\sql\db.sqlite
- AppData\Roaming\Signal\config.json
Analyzing Signal Artifacts with ArtiFast Signal
As the name indicates, ArtiFast Signal is solely dedicated to analyzing Signal artifacts. To be able to extract Android/iOS Signal data with ArtiFast Signal a full file system image of the device is required. After you have created your case and added evidence for the investigation, at the Artifacts Parser Selection Phase, you can select from Signal Artifacts:
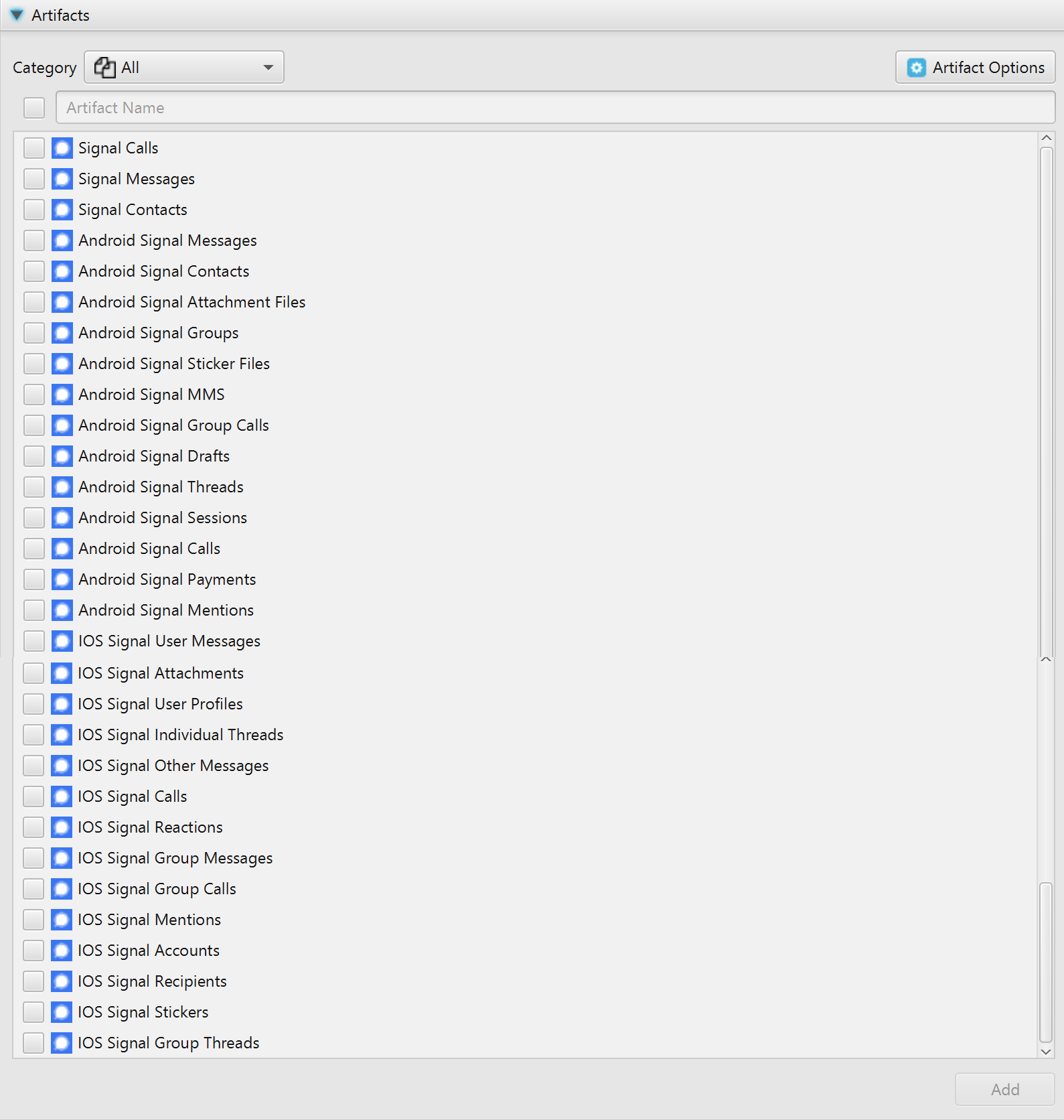
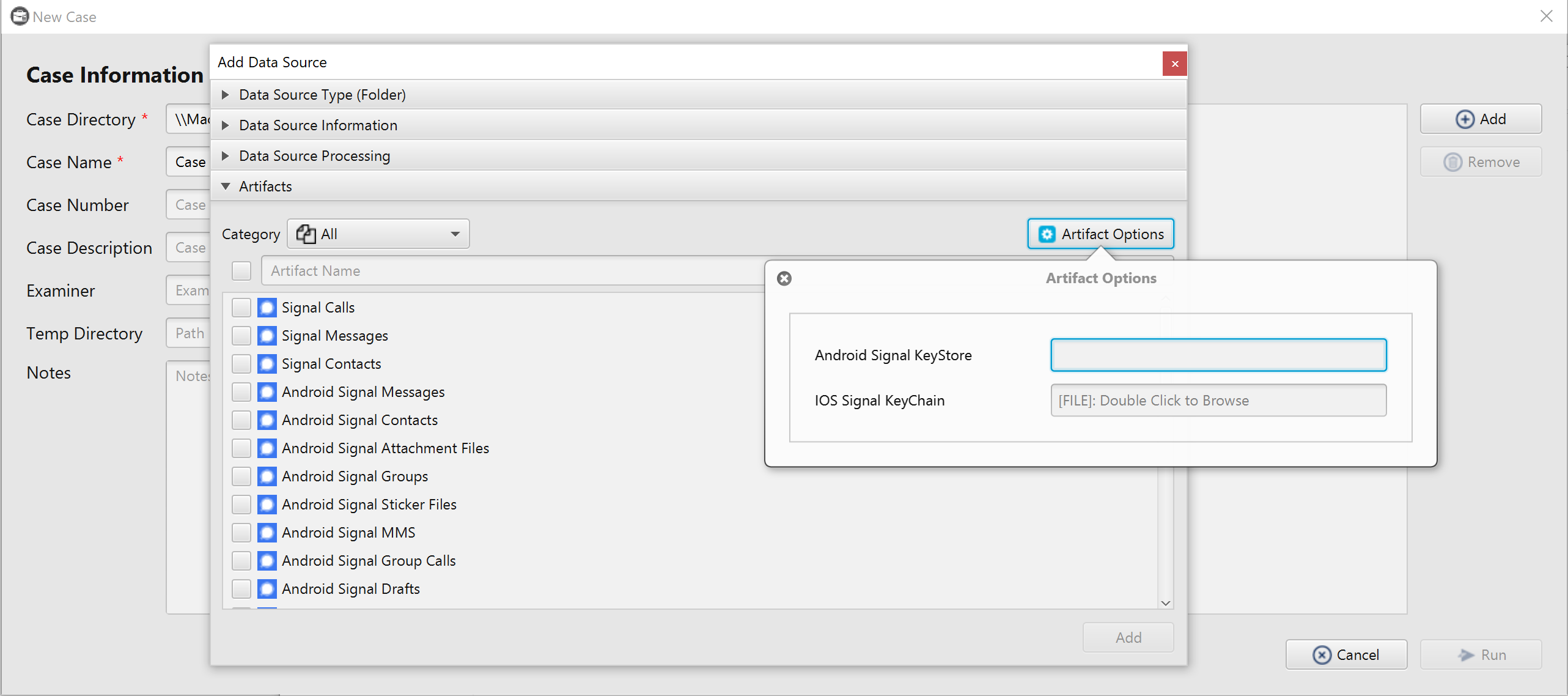
In addition to the full file system image, iOS Keychain/Android Keystore entries should be extracted. So, before parsing Signal artifacts, the user should select the corresponding iOS Keychain file or Android Keystore file/folder by clicking on the Artifact Options button, which is located to the top right of the search box. The iOS Keychain formats supported by ArtiFast Signal are listed below:
- Keychain-Dumper output (Ex. keychain_dumper.txt).
- UFED Touch 2 output (Ex. backup_keychain_v2.plist).
- UFED PA reports (Ex. Report.xml).
- Elcomsoft output (Ex. Elcomsoft_keychain_(NULL)_20210701_131834Z.xml).
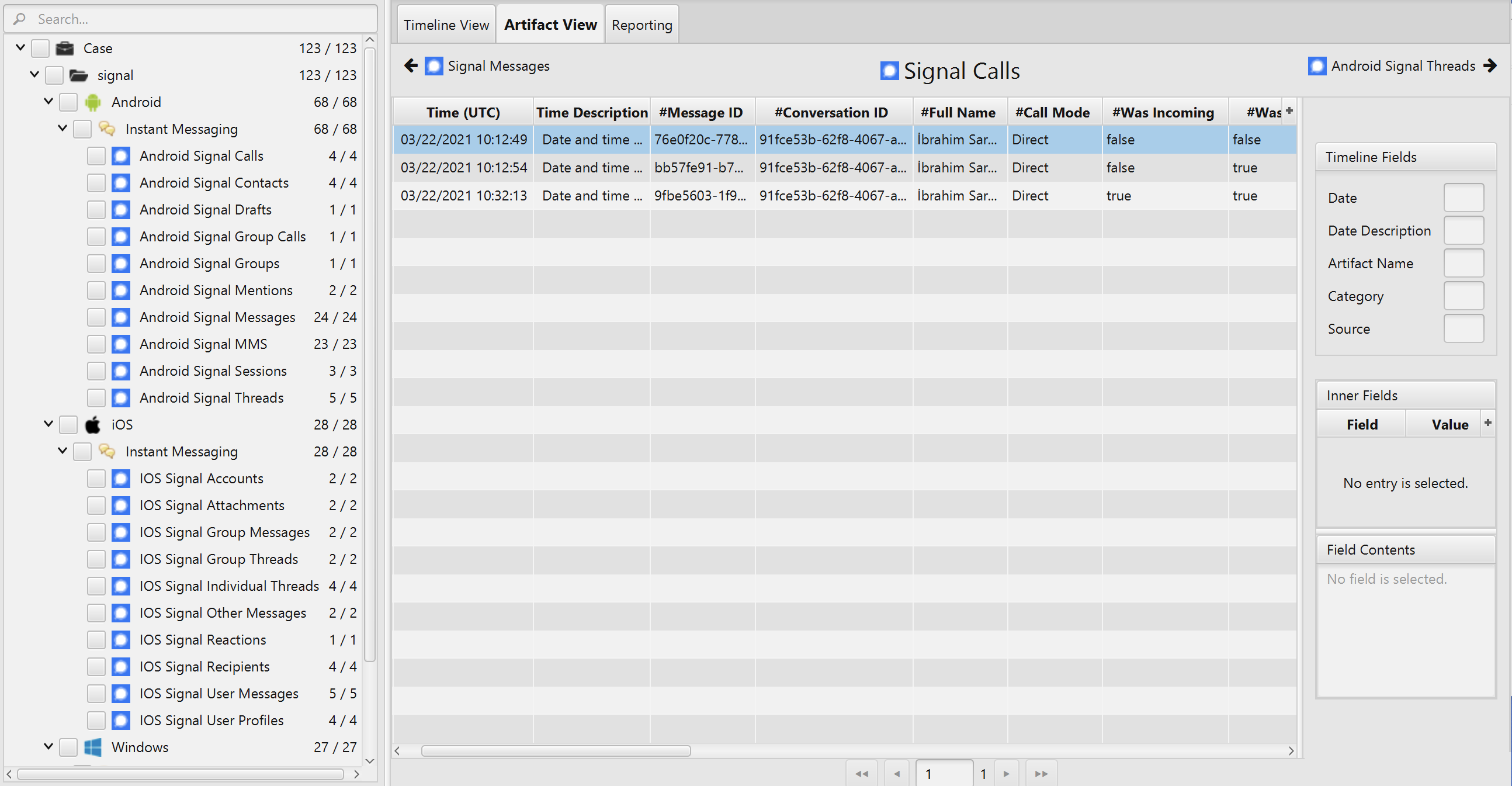
Once ArtiFast Signal parser plugins complete processing artifacts for analysis, it can be reviewed via "Artifact View" or "Timeline View," with indexing, filtering, and searching capabilities.
