Investigating TeamViewer
08/11/2021 Monday
TeamViewer is a software that allows remote access and control of computers and other devices. It is known for being reliable, fast, easily accessible, and for the use of secure digital communication technology. TeamViewer is mainly used in web conferencing and remote administration, and it is available for desktop (Windows, macOS, and Linux) and mobile devices (Android and iOS).
Digital Forensics Value of TeamViewer Artifacts
TeamViewer forensics can provide critical data as it helps in identifying successfully connected incoming and outgoing sessions, their related information, failed connection attempts, IDs, public IPs, and so much more potential evidential data that would aid in finding suspicious activities, that then could lead to possible suspects.
Location of TeamViewer Artifacts
TeamViewer artifacts are stored in the following locations:
C:\Program Files\TeamViewer\Connections_incoming.txt
C:\Users\<user>\AppData\Roaming\TeamViewer\Connections.txt
C:\Program Files\TeamViewer\TeamViewer<version>_logfile.log
Structure of TeamViewer Artifacts
TeamViewer saves connection data in log files, the TeamViewer<version>_logfile.log file is intended
for staff members as it is used for analyzing past actions, technical troubleshooting, and bug detection. It
contains information such as outgoing and incoming connections, machine information, denied connections, and
it uses local time from the computer.
Connections_incoming.txt and connections.txt log files are both structured in an easy user-readable format.
Connections_incoming.txt log file contains information about all successful incoming connections, such as
the auto-generated unique TeamViewer ID, device display name, and uses UTC. Whereas connections.txt log file
records all outgoing connections from a machine, and it also uses UTC.
Analyzing TeamViewer Artifacts with ArtiFast Windows
This section discusses how to use ArtiFast Windows to analyze TeamViewer artifacts from Windows
machines and what kind of digital forensics insight we can gain from the artifacts.
After you have created your case and added evidence for the investigation, at the Artifacts Selection phase,
you can select TeamViewer artifacts:
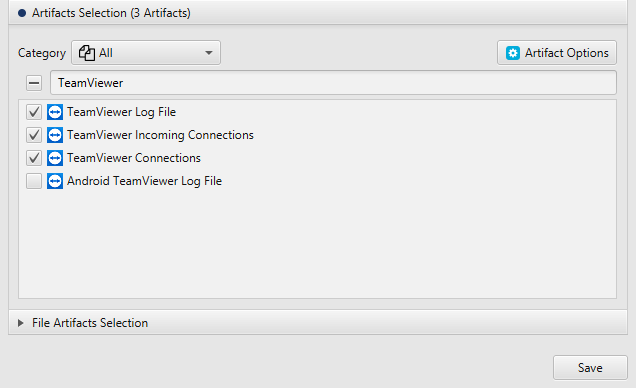
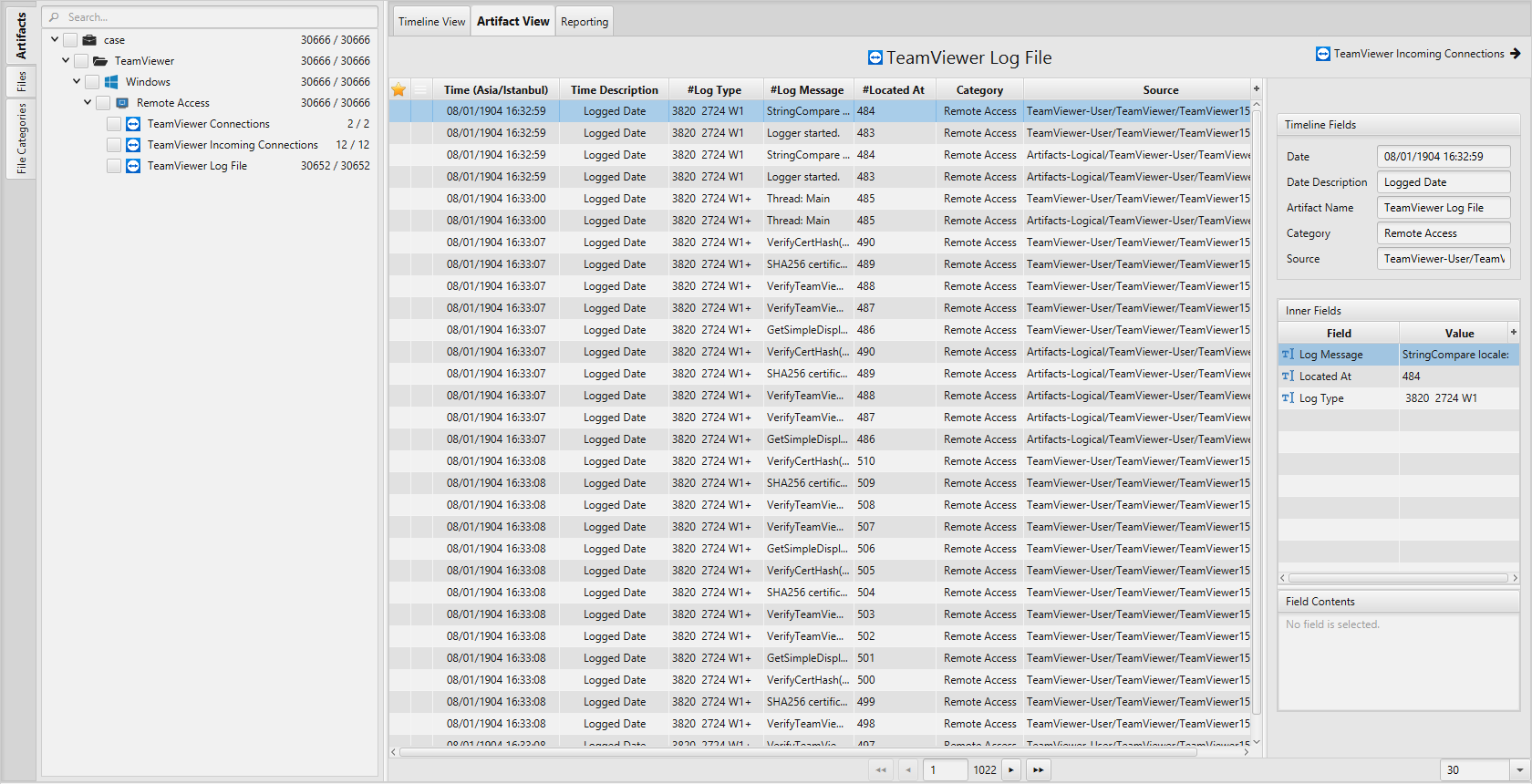
Once ArtiFast parser plugins complete processing artifacts for analysis, it can be reviewed via “Artifact View” or “Timeline View”, with indexing, filtering, and searching capabilities. Below is a detailed description of TeamViewer artifacts in ArtiFast Windows.
TeamViewer Log File Artifact
The artifact extracts Windows TeamViewer log file information.
- Last Archived - Last archived file name.
- Logged Date - Logged date and time.
- Log Type - Log type.
- Log Message - The logged message.
- Located At - Located at.
TeamViewer Incoming Connections Artifact
The artifact extracts Windows TeamViewer incoming connections.
- Connected TeamViewer ID - Connected TeamViewer ID.
- Connection Start Date - The date and time the connection started.
- Connection End Date - The date and time the connection ended.
- Connected Device Name - The connected device name.
- Connected User Name - The connected user name.
- Connection Type - Connection type.
- Connection Unique ID - Connection unique Id.
- Located At - Located at.
TeamViewer Connections Artifact
The artifact extracts Windows TeamViewer connections.
- Connected TeamViewer ID - Connected TeamViewer Id.
- Connection Start Date - The date and time the connection started.
- Connection End Date - The date and time the connection ended.
- Connected User Name - The connected user name.
- Connection Type - Connection type.
- Located At - Located at.
For more information or suggestions please contact: lina.alsoufi@forensafe.com
