Investigating Windows Services
12/11/2021 Friday
Windows Services is a key component of the Windows operating system that allows long-running processes to be created and managed in their own sessions. These services start running in the background usually on system boot without any user interaction and can continue to run long after the user has signed off the system. A broad range of functions are handled by these services including, data backup, network connections, user credentials, and more. Developers opt to use these services for functions required to run in the background without user interference, they do so by creating applications that can be installed as a Windows service.
Digital Forensics Value of Windows Services Artifacts
Numerous amounts of malware and worms in the wild utilize Windows services, as the component provides desirable features such as persistence. Bad actors can have their malware create new services or replace existing ones and these services could be rootkits, backdoors etc. Analysis of the Windows services artifact can help in finding evidence of persistent malware.
Location of Windows Services Artifacts
Windows services artifact source file is located at C:\Windows\config\SYSTEM. Within the SYSTEM hive, the artifact data can be found at the location: CurrentControlSet\Services
Structure of Windows Services Artifacts
The SYSTEM file, which contains the Windows services artifact, is a registry hive. This is a database where necessary operating system and\or application configurations are maintained. It is made up of keys and values. Keys can be containers that may contain other subkeys. Keys point to values that have variable length data sets. Windows provides an executable file called regedit.exe that can be used to view and make changes to the registry database.
Analyzing Windows Services Artifacts with ArtiFast Windows
This section will discuss how to use ArtiFast Windows to extract Windows Services artifact from Windows
machines and what kind of digital forensics insight we can gain from the artifact.
After you have created your case and added evidence for the investigation, at the Artifact Parser selection
phase, you can select Windows services artifact:
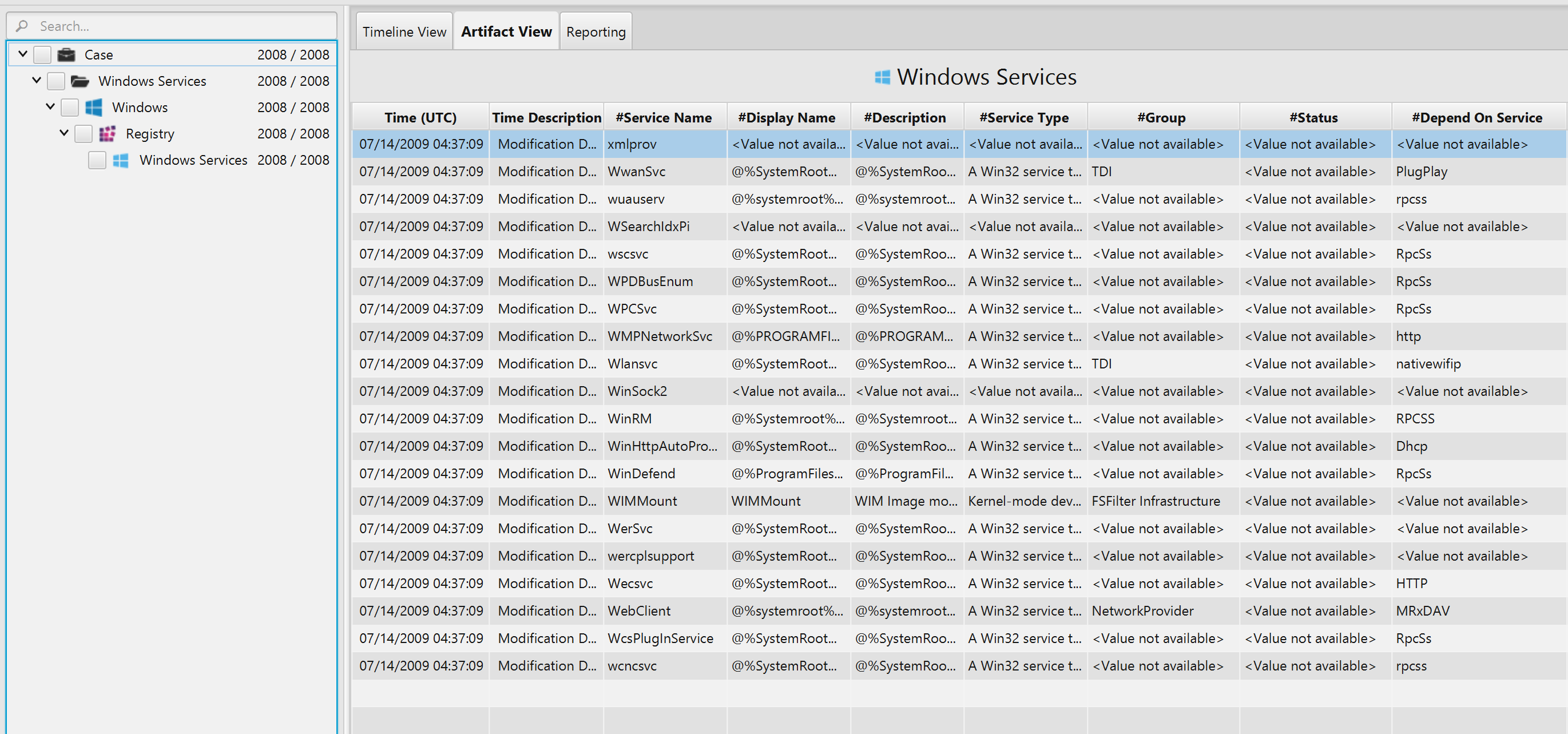
Once ArtiFast parser plugins complete processing the artifact for analysis, it can be reviewed via “Artifact View” or “Timeline View,” with indexing, filtering, and searching capabilities. Below is a detailed description of the Windows Services artifact in ArtiFast software.
Windows Services Artifact
The artifact contains information on the current services
that are on a specific system. The details you can view include:
- Driver ID - The ID of the driver.
- Service Name - The service name.
- Display Name - The display name for the service.
- Description - Description of the service.
- Service Type - The service type.
- Group - Group the service belongs to.
- Status - Status of the service.
- Depend on Service - Service dependencies.
- Error Control - Actions for error control on the service.
- Image Path - Path to executable.
- Object Name - Displays user account.
- Required Privileges - Required privileges to run this specific service.
- Start Type - This defines when in the boot sequence the service is started.
- Failure Actions - The configured actions on failure of the service.
- Delayed AutoStart - This indicates whether the service should be delayed from starting until other automatically started services are running.
- Tag - The value of Tag specifies a number that is unique within the group of which the service is a member.
- Service DLL Location - Service DLL file location on the system.
- Other Service Parameter Names - Other service parameter names.
- Located At - Location of the service in the registry hive.
- Modification Date - Service last modification date and time.
For more information or suggestions please contact: ummulkulthum.wambai@forensafe.com
